If you’ve run Linux long enough, you’ve probably seen the trick: type 10.68 and it resolves to 10.0.0.68, or 10.20.2 lands on 10.20.0.2. In a lab this can save keystrokes; in production it can turn into a debugging nightmare. Here’s why it works, where it still works, where it won’t, and how to manage it responsibly in modern Linux environments.
Not Sorcery—Legacy IPv4 Parsing
This behavior comes from historical IPv4 socket APIs (inet_addr(), inet_aton()), which accept abbreviated formats in addition to the canonical dotted quad a.b.c.d. Many Unix tools built on those APIs inherited the behavior:
a.b.c→ the last fieldcis treated as 16 bits (two octets).10.20.2≡10.20.0.2.a.b→ the last fieldbis treated as 24 bits (three octets).10.68≡10.0.0.68.a(single integer) → full 32-bit address.167772161≡10.0.0.1.
When octets are “missing,” they’re left-padded with zeros inside the 16/24/32-bit chunk. That’s why ping 10.68 often ends up at 10.0.0.68.
Where This Still Works on Linux
It depends on the binary and which API it uses:
- Classic tools (
ping, legacytelnet,ssh, some builds ofcurl) may accept abbreviated forms because they call tolerant resolvers or legacyinet_*functions. - Modern utilities/libraries that use
getaddrinfo()andinet_pton()tend to be strict: they requirea.b.c.dor a FQDN. Many SDKs and runtimes (Go, Rust, Pythonipaddress, modern Java) are strict by design. - Browsers and many HTTP clients tightened parsing in recent years; some reject abbreviated IPv4 to avoid security pitfalls.
Bottom line: what works in one TTY can fail in another tool, container, or pipeline. For a sysadmin, that inconsistency is the risk.
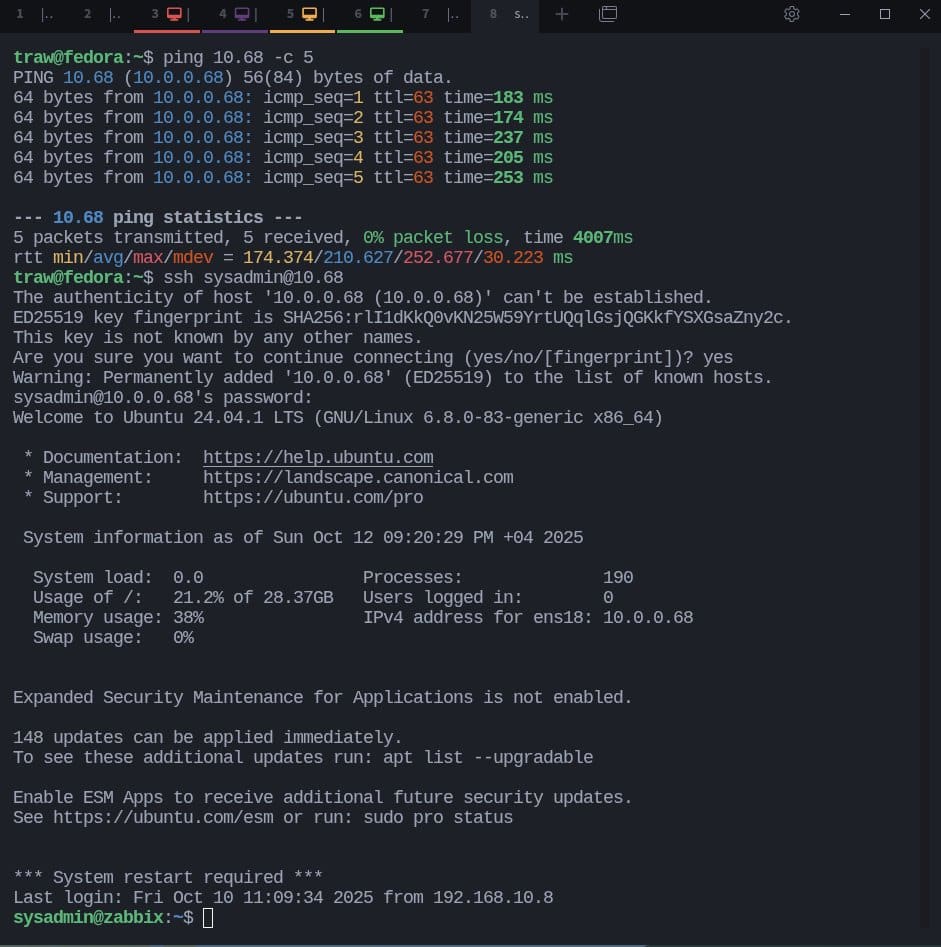
The Gotchas You Should Know
1) Leading Zeros, Octal, and Hex—A Minefield
Legacy parsers historically accepted multiple bases:
010as octal →80x10as hex →16
This has led to real WAF/SSRF bypasses and ACL confusion. Example: 010.000.000.001 may resolve to 8.0.0.1. Golden rule: avoid leading zeros and non-decimal bases.
2) It Doesn’t Apply Everywhere
- CIDR, routes, and netmasks do not support shorthand.
10.0.0.0/24must be written in full. - Docs, tickets, inventory, ACLs, firewalls: mixing short forms breeds ambiguity and tech debt.
- Logs and audits: always normalize to four octets.
3) Operational Security
Attackers can abuse parser differences between components (strict proxy vs. permissive backend) to slip past validation. Reduce attack surface by standardizing representations.
Linux Team Best Practices
Production: Canonical or Nothing
- Always use
a.b.c.din configuration (systemd-networkd, NetworkManager,iproute2,nftables,keepalived, BIRD, FRR, etc.). - No leading zeros (
10.0.0.1, not010.000.000.001). - Do not use shorthand in scripts, playbooks, or IaC (Ansible, Terraform, Helm).
CI/Pre-commit Normalization
Add a lightweight check that rejects non-canonical addresses in network changes:
# crude detector for non-canonical IPv4 (illustrative)
grep -RhoE '\b([0-9]+(\.[0-9]+){0,3})\b' ./configs \
| awk '
function valid(o){return (o>=0 && o<=255)}
{
n=split($0,a,".");
if (n!=4) { print "Non-canonical:", $0; next }
bad=0
for (i=1;i<=4;i++) if (!valid(a[i])) bad=1
if (bad) print "Out of range:", $0
}'
Code language: PHP (php)Or rely on strict parsers:
# Canonicalize/validate with Python 3
import ipaddress, sys
for line in sys.stdin:
for tok in line.split():
try:
ip = ipaddress.IPv4Address(tok)
print(str(ip))
except:
pass
Code language: PHP (php)Live Checks & Linters
getent ahosts 10.68shows how glibc resolves it on that host.python3 - <<'PY'\nimport ipaddress; print(ipaddress.ip_address("10.68"))\nPYwill fail (strict), useful to detect shorthand that slipped in.- Tools like
ipcalcinsist on canonical input—great for pipelines.
Put It in the Runbook
Add a note to operational docs: “CLIs may accept abbreviated IPv4 for compatibility; the supported format in this environment is a.b.c.d only.” Prevent newcomers from “optimizing” a playbook with shorthand.
Handy “Cheat Sheet” (for Internal Education)
a.b.ccis 16 bits:10.20.2→10.20.(2>>8).(2&255)→10.20.0.2a.bbis 24 bits:10.68→10.(68>>16).((68>>8)&255).(68&255)→10.0.0.68a(32-bit integer)(a>>24).((a>>16)&255).((a>>8)&255).(a&255)
Use it to explain the behavior—not to justify production use.
Linux Tools: Who’s Strict, Who’s Tolerant (Typical Landscape)
- Often tolerant (build-dependent):
ping/ping6(iputils), OpenSSH’sssh, traditionalnc, somecurl/wgetbuilds depending on resolver. - Strict: Go’s
net.ParseIP, Rust’sstd::net, Python’sipaddress, many systemd units, modern Java libs, most cloud SDKs and web APIs,iptables/nftables(rules expecta.b.c.d), browsers.
This varies by distro, version, and compile flags—don’t assume homogeneity.
Useful Internal Demos
Show the Leading-Zero Trap (Octal)
# On systems with legacy inet parsing:
ping -c1 010.000.000.001 # may hit 8.0.0.1 (danger!)
# Strict tools will reject it:
python3 - <<'PY'
import ipaddress
try: print(ipaddress.ip_address('010.000.000.001'))
except Exception as e: print("Error:", e)
PY
Code language: PHP (php)Normalize a Legacy Host List
# Extract and validate all IP-like tokens from hosts.txt
awk '{for(i=1;i<=NF;i++) if ($i ~ /^[0-9.]+$/) print $i}' hosts.txt \
| while read ip; do
python3 - "$ip" <<'PY'
import sys, ipaddress
try:
print(ipaddress.ip_address(sys.argv[1]))
except:
print("INVALID:", sys.argv[1])
PY
done | sort -u
Code language: PHP (php)Network/SRE Policy Template
- Canonical format required across config repos, CMDB, and IaC.
- CI block for non-canonical or leading-zero addresses.
- Automated conversion for legacy inventories with a strict validator.
- Runbooks explaining when shorthand may appear (ad-hoc CLI in labs) and why it’s not accepted in PRs.
- Security tests: add shorthand/oct/hex IPv4 cases to WAF/SSRF and input-validation test suites.
What About IPv6?
Different story. IPv6 compression is standardized (::, suppress leading zeros per hextet, only one ::, etc.). Don’t confuse IPv6 compression with legacy IPv4 shorthand—different rules, different rationale.
Conclusion
Abbreviated IPv4 addresses are a legacy convenience that can break assumptions in modern production systems. A professional Linux team should:
- Understand why
10.68resolves to10.0.0.68. - Avoid shorthand in anything that touches configuration, automation, documentation, or security.
- Normalize and validate systematically in CI/CD.
- Educate the team about leading zeros, octal, and hex pitfalls.
Save keystrokes where it doesn’t matter; avoid surprises where it does.
FAQ
How can I expand abbreviated IPv4 to canonical form in a script?
Use strict parsers. In Python, ipaddress.IPv4Address('10.68') will raise, which is useful to catch bad input. If you must expand, pre-parse into a.b → a.0.0.b and a.b.c → a.b.(c>>8).(c&255), then validate with ipaddress and output a.b.c.d.
Can I use shorthand in iptables/nftables or ip route?
Don’t. Engines expect the canonical dotted quad. Stick to 10.0.0.68/32, not 10.68/32.
Why does curl accept 10.68 on one host and reject it on another?
Likely different resolver stacks or build options (glibc vs. c-ares, different libcurl). Never rely on identical behavior across distros, containers, or base images.
How do I detect non-canonical IPs in our repos?
Add a pre-commit or CI job that scans for ^[0-9.]+$, rejects anything that isn’t exactly four octets in range 0–255, and flags leading zeros. Back it with a strict validator such as Python’s ipaddress.

