The closure affects both commercial products and free software, including the widely used CSF firewall. The server administration community braces for impact.
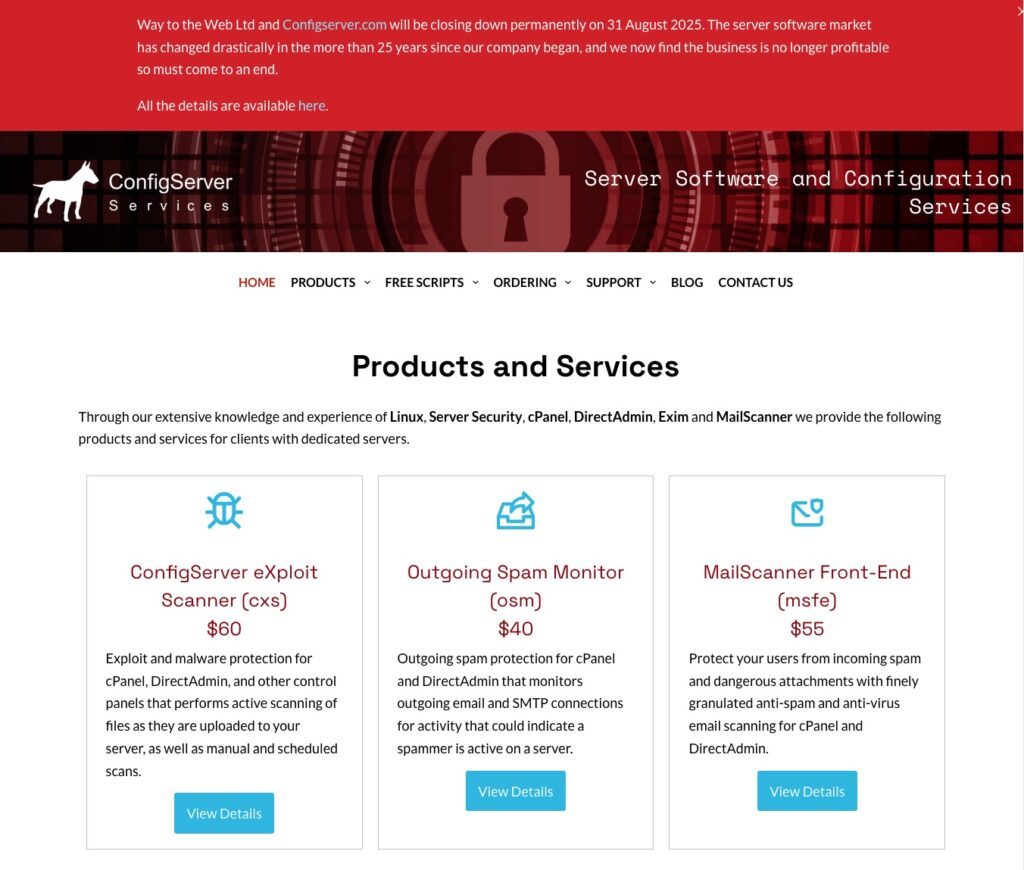
Way to the Web Ltd., the company behind ConfigServer.com, has announced it will permanently cease operations on August 31, 2025. After more than 25 years of providing server security solutions for Linux environments, the company will shut down its entire platform, ending support, updates, and downloads for all its software tools.
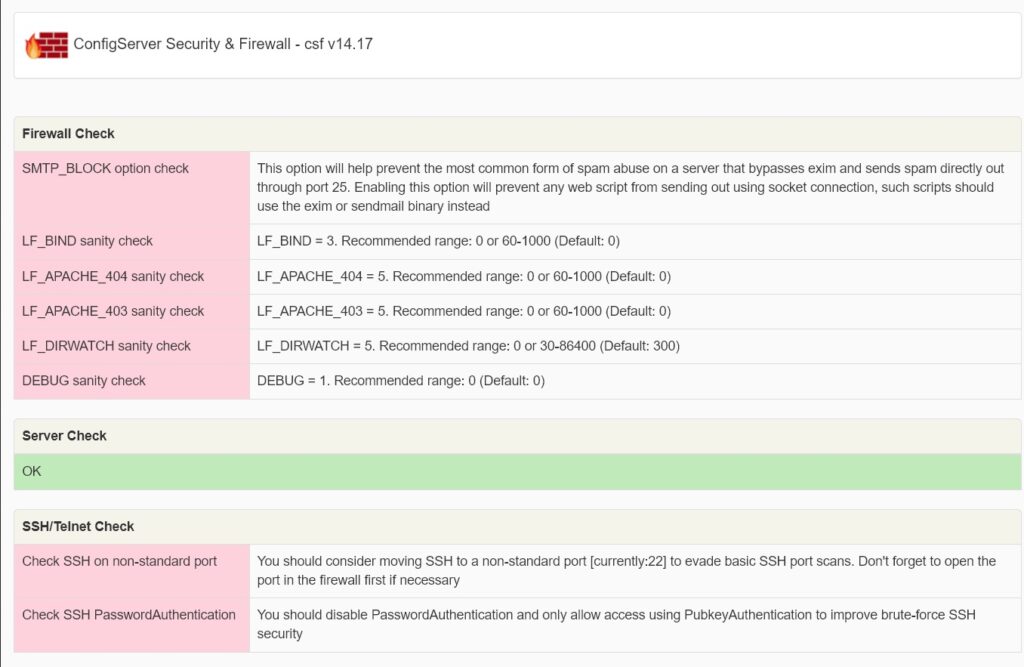
The announcement has caused significant concern among system administrators who have relied for years on solutions like ConfigServer Security & Firewall (CSF), a staple in control panels such as DirectAdmin and cPanel. Other tools affected by the shutdown include ConfigServer Exploit Scanner (cxs), MailScanner Front-End (MSFE), Outgoing Spam Monitor (osm), ConfigServer Mail Queues (cmq), Mail Manage (cmm), ModSecurity Control (cmc), and ConfigServer Explorer (cse).
End of Support: What It Means in Practice
Starting August 31, users will no longer be able to:
- Download any software from ConfigServer’s official servers.
- Change license IPs for commercial products.
- Activate or reinstall software that requires license verification.
- Submit support tickets or access the official support forum.
- Receive updates or new exploit fingerprints (e.g. for CXS).
In the case of commercial software like cxs, osm, and MSFE, failure to upgrade to the latest version before the shutdown will render them unusable, as their license servers will be offline and impossible to reach.
What About the CSF Firewall?
The widely used ConfigServer Security & Firewall (CSF), while free, will also no longer receive updates or be available for download. However, the developers have stated that they are working to release CSF under a GPLv3 open-source license before shutting down, which would allow the community to maintain and host it via platforms like GitHub.
In community forums such as DirectAdmin, users are already discussing alternatives like UFW, Fail2ban, or setting up private repositories to host CSF locally for future installations. However, CSF’s incompatibility with newer operating systems like AlmaLinux 10 poses a significant obstacle to its long-term viability.
Security experts have also warned of the risks of keeping references to configserver.com in default settings after the domain is no longer maintained, as domain hijacking could be exploited to serve malicious content. It is strongly advised to update the /etc/csf/downloadservers file to point to a trusted domain to avoid potential compromise.
A Closure That Reflects Broader Industry Trends
According to the official statement, the decision stems from drastic changes in the server software market that have made the business unviable. As the company explained: “The server software market has changed drastically since we started more than 25 years ago, and the business is no longer profitable, so it must come to an end.”
Users had already sensed the company’s direction, with months of no updates or engagement in the support forums. The abrupt nature of the announcement and lack of an official successor has left many administrators facing uncertainty.
What Can Users Do Before August 31?
- Update all products to their latest version before the shutdown date.
- Download and archive installation files for future use.
- Disable automatic updates in CSF to avoid errors after August.
- Evaluate alternative security solutions compatible with modern systems.
The community is already exploring forks and successor projects. If CSF is indeed released under an open-source license, it could pave the way for future community-driven development.
The closure of ConfigServer marks the end of an era in Linux server security administration, leaving behind a loyal user base and a lasting legacy in the open-source cybersecurity landscape.