It’s 2025, and email access via IMAP still works the same way it did in 1999. The protocol lacks native support for two-factor authentication (2FA), making it a weak link in many infrastructures. But that doesn’t mean it’s unfixable. With the right architectural approach, IMAP can be secured—without surrendering control to Microsoft or Google.
Table of Contents
1. The Problem: IMAP and the Absence of 2FA
IMAP (Internet Message Access Protocol) remains widely used in mail servers such as Dovecot, Cyrus, or Courier. But it has a fundamental flaw: it does not natively support two-factor authentication.
If an attacker has valid credentials, they can log in. That’s it.
No second factor, no one-time codes, no push notifications.
It’s not a matter of misconfiguration — IMAP was simply never designed to support MFA flows.
In an age where credential leaks are common and email accounts are often the gateway to lateral movement or fraud, this is a serious security issue.
2. Regulatory Pressure Meets Legacy Tech
Compliance frameworks like ENS, NIS2, ISO/IEC 27001, and even GDPR security principles increasingly demand MFA for any exposed service.
A public-facing IMAP server that relies solely on username and password clearly fails these standards.
And here’s the industry’s default solution:
“Migrate to Microsoft 365 or Google Workspace. They offer MFA, anomaly detection, audit trails. Problem solved—just pay the license.”
But that recommendation raises serious concerns:
- Loss of control and data sovereignty
- Vendor lock-in
- Cost escalation
- Security monoculture
So, what can we do if we want security without surrendering control?
3. Stop Thinking About Products. Start Thinking Architecture.
The issue isn’t just IMAP lacking 2FA. The real issue is exposing IMAP to the internet without compensating controls.
We can’t retrofit 2FA into the protocol. But we can control access to it, using proven architectural patterns.
4. Practical Options to Secure IMAP Access in 2025
Here’s how to lock down IMAP while keeping full control of your infrastructure:
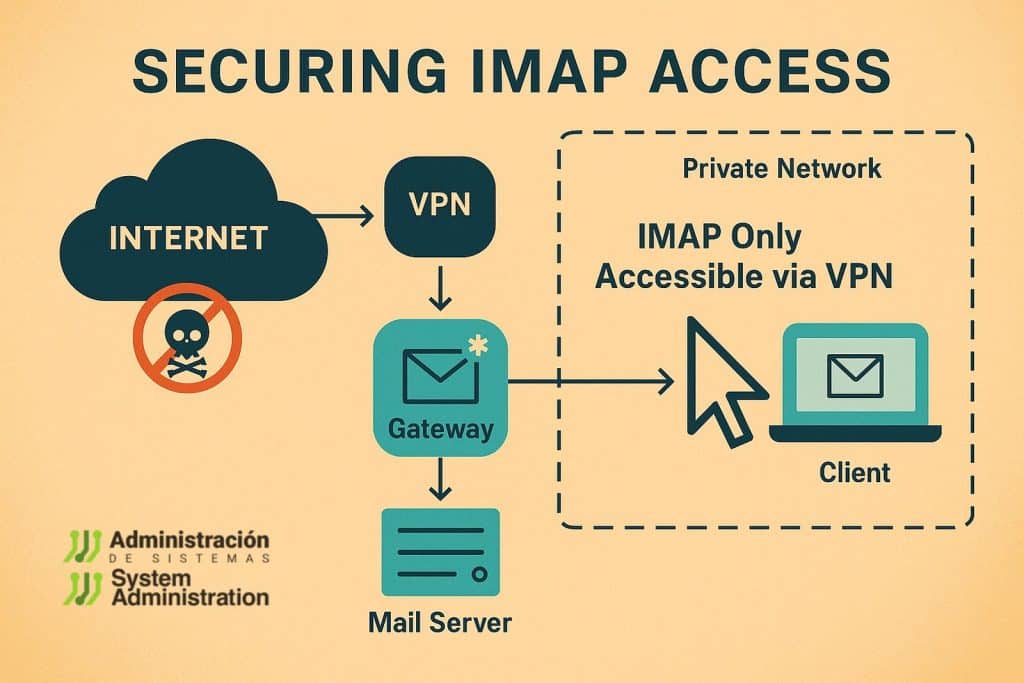
Option 1: VPN with 2FA + Internal IMAP Access Only
Architecture:
- IMAP server (e.g. Dovecot) accessible only within a private network.
- Remote access requires VPN connection secured with 2FA.
- Clients (desktop, mobile) must connect to the VPN first.
Recommended Tools:
- WireGuard or OpenVPN
- VPN portals with MFA: Pritunl, Tailscale, etc.
- 2FA via TOTP, hardware tokens, SAML or WebAuthn
Advantages:
- Strong MFA at the network layer
- IMAP is not publicly exposed
- Full infrastructure control
- Meets security standards like ENS, NIS2, CIS Benchmarks
Option 2: Webmail with MFA + Internal IMAP Only
Architecture:
- IMAP is accessible only to the webmail interface (localhost or internal LAN).
- Users access email via browser with MFA.
- No direct IMAP access from external clients.
Suggested Tools:
- Roundcube with TOTP/MFA plugins
- Rainloop or [Zimbra OSS]
- Reverse proxies for added control (e.g. NGINX, Traefik)
Advantages:
- End-user experience similar to cloud providers
- MFA enforced at the web layer
- No IMAP exposure to the internet
Option 3: SMTP Gateway + Filtering + Log Monitoring
Even if IMAP is internal, your SMTP gateway must be secured:
- Use mail filters like Proxmox Mail Gateway, Rspamd, or MailCleaner.
- Monitor authentication logs using SIEM tools: Wazuh, ELK, Graylog
- Implement brute force protections: Fail2ban, CrowdSec, GeoIP bans
Note: These are complementary, not replacements for MFA.
Option 4: Zero Trust Access via Identity-Aware Proxies
For organizations ready to go further:
- Use Cloudflare Access, [Tailscale ACLs], or Teleport to proxy IMAP behind a policy engine.
- Enforce identity-based access with conditional logic.
While not trivial to implement, this provides a high-security model similar to Google BeyondCorp.
5. What You Shouldn’t Do
- Expose IMAP ports (143/993) directly to the internet
- Rely on complex passwords alone
- Assume firewalls are sufficient
- Believe that monitoring compensates for lack of access control
6. Architecture Comparison Table
| Strategy | 2FA Protected | Internet Exposure | Compliance Ready | Complexity | Ideal Use Case |
|---|---|---|---|---|---|
| VPN + Internal IMAP | Yes | No | Yes | Medium | SMBs, agencies, privacy-focused |
| Webmail + MFA + Internal IMAP | Yes (via web) | No | Yes | Low | Remote-first teams |
| Mail Gateway + Logging | No | Partially | No | Low | Supplemental control |
| Cloud Email (M365/GWS) | Yes | Yes | Yes | None | Organizations with no IT team |
7. Final Thoughts: Design First, React Less
IMAP will never support 2FA. But access to IMAP can absolutely be protected with well-known, cost-effective, and standards-aligned methods.
“Most of today’s cybersecurity efforts are band-aids for poor infrastructure design.”
This is a textbook example.
You don’t need to jump into ZTNA overnight.
You don’t need to send all your email to Silicon Valley.
You do need to stop exposing critical services without layered protection.
Recap: How to Secure IMAP in 2025 Without Selling Your Soul
- Never expose IMAP directly to the internet.
- Put it behind a VPN or a webmail proxy with MFA.
- Harden your SMTP gateway and monitor logs.
- If you can, adopt a Zero Trust overlay.
- Above all: design with segmentation, identity, and access control in mind.
Email isn’t going away. But if we’re still treating it like it’s 1999, we’re failing in 2025.