While IO_uring has been hailed as one of the most significant advancements in the Linux kernel over the past decade — delivering exceptional performance improvements for asynchronous I/O operations — it has also raised notable security concerns. With the upcoming release of Linux 6.6, system administrators will finally have a straightforward way to disable IO_uring globally via a simple sysctl setting, without needing to patch or recompile the kernel.
IO_uring: A Double-Edged Sword
Introduced to streamline and accelerate non-blocking I/O, IO_uring has become a foundational technology for modern Linux systems, particularly for high-performance applications like databases and networking tools.
However, it hasn’t come without risks. Google recently disclosed that around 60% of the vulnerabilities reported through its Vulnerability Rewards Program were related to IO_uring, leading the company to restrict or disable IO_uring across its infrastructure, including Google servers, Android devices, and ChromeOS.
These concerns have been amplified when considering older kernel versions, where IO_uring’s integration with the Linux security subsystem has been less robust.
A New sysctl: io_uring_disabled
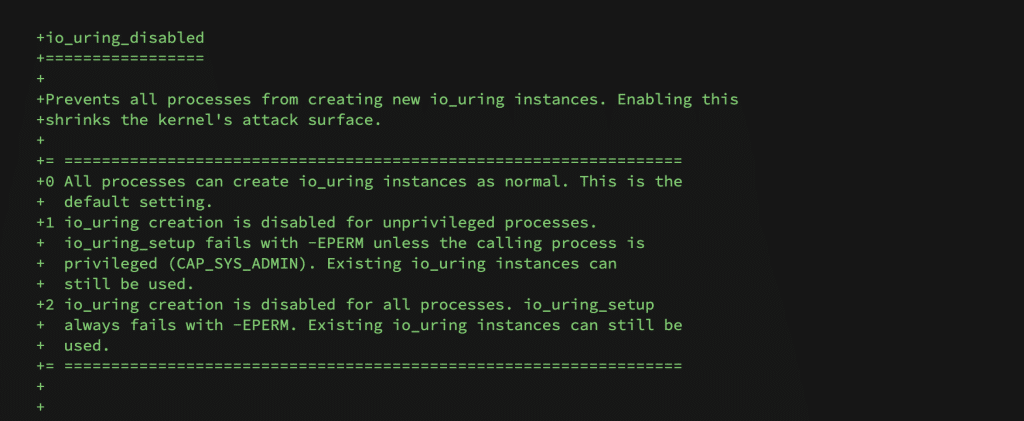
Submitted by Matteo Rizzo (Google) and merged into the for-6.6/io_uring branch, a new sysctl parameter — io_uring_disabled — will allow administrators to control IO_uring system-wide with three simple modes:
- 0 (default): All processes can freely create IO_uring instances (current behavior).
- 1: Only privileged processes (with
CAP_SYS_ADMIN) can create new IO_uring instances. - 2: Completely blocks all processes, including privileged ones, from setting up IO_uring instances.
This change significantly reduces the attack surface by allowing system administrators to selectively or entirely block IO_uring based on the security needs of their environments.
How To Disable IO_uring
Once running Linux 6.6 or newer, administrators can disable IO_uring instantly by setting the sysctl value:
sudo sysctl -w kernel.io_uring_disabled=2To make the setting persistent across reboots, add it to /etc/sysctl.conf:
kernel.io_uring_disabled = 2Alternatively, if you prefer to restrict only unprivileged users while still allowing root or admin processes to utilize IO_uring, setting the value to 1 provides a more nuanced balance.
Why This Matters
The ability to disable IO_uring easily is crucial for environments with stringent security requirements, such as:
- Public-facing servers
- Cloud infrastructures
- Critical enterprise systems
- Embedded and IoT devices with minimal security margins
By limiting or disabling IO_uring, administrators can minimize potential exposure to yet-undiscovered vulnerabilities, adhering to the security principle of least privilege: only enabling complex subsystems where they are explicitly needed.
IO_uring Remains Important, But With Caution
It’s important to note that IO_uring remains a powerful and efficient I/O interface for Linux, particularly in workloads demanding low latency and high throughput. The addition of this sysctl does not diminish IO_uring’s utility — rather, it provides administrators with better control over its deployment.
In trusted, well-audited environments, IO_uring can continue delivering major performance gains. In contrast, in sensitive or untrusted setups, administrators can now easily opt to disable it without recompiling kernels or applying custom patches.
Conclusion
The inclusion of the io_uring_disabled sysctl in Linux 6.6 demonstrates the Linux community’s ongoing commitment to balancing innovation with security. Administrators finally have a simple and effective tool to manage IO_uring usage according to their risk models — enhancing the security posture of Linux systems without sacrificing the flexibility and power the platform is known for.
More info: Kenerl list and Phronix.