NETinVM represents a fundamental tool for system administrators seeking a robust and realistic laboratory environment for learning and testing network technologies. This technical guide delves into the capabilities, architecture, and advanced use cases of this nested virtualization platform.
Technical Environment Architecture
Base Infrastructure and Core Services
The base machine (base.example.net) acts as the central controller of the environment, providing critical infrastructure services. The DHCP service manages automatic IP address assignment using specific pools for each network segment, while the DNS server resolves internal names through forward and reverse zones configured for the example.net domain. The NTP service ensures temporal synchronization between all nodes, a crucial aspect for correlated logs and valid SSL certificates.
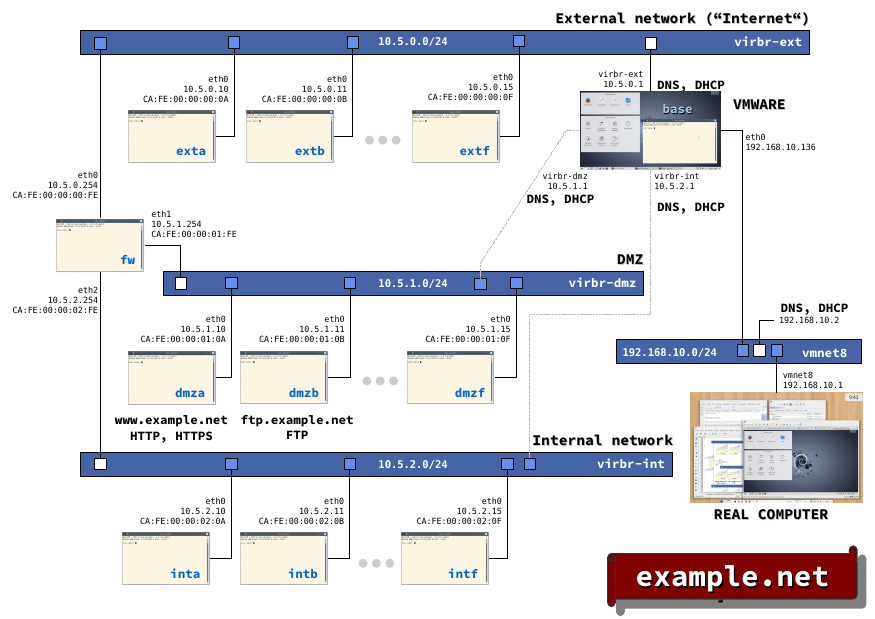
Network Segmentation and Topology
The design implements a three-tier topology that replicates real enterprise environments:
External Network (ext): Simulates the public Internet segment with simulated public addressing. Includes nodes that emulate external services and allows testing of outbound connectivity, default route configuration, and cloud service simulation.
Demilitarized Zone (DMZ): Implements the perimeter network concept with two specialized servers. The dmza server runs Apache with enabled SSL modules, configurable self-signed certificates, and virtual hosts for web application testing. The dmzb server provides FTP services with vsftpd, supporting both active and passive FTP, virtual users, and secure FTPS transfers.
Internal Network (int): Represents the protected corporate segment with restricted access through SSH, simulated internal services, and strict security policies that prevent direct access from external networks.
Firewall and Routing Component
The fw node acts as a multihomed gateway implementing advanced filtering and routing functionalities. It uses iptables or nftables depending on configuration, supports dynamic and static NAT, implements stateful filtering rules (stateful inspection), and allows IPSec site-to-site VPN configuration. The system includes detailed logging capabilities, rate limiting to prevent DDoS attacks, and basic QoS support.
Advanced Use Cases for Administrators
Firewall Configuration and Hardening
Administrators can practice implementing complex security policies, including granular filtering rules by ports, protocols, and source/destination addresses. The environment allows testing fail2ban configurations for brute force attack protection, port knocking implementation for critical services, and transparent proxy configuration with Squid for web content filtering.
VPN Infrastructure Implementation
NETinVM supports multiple VPN technologies for diverse scenarios. Administrators can configure OpenVPN with PKI certificates, implement IPSec tunnels with strongSwan, establish high-performance WireGuard connections, and create overlay networks with technologies like VXLAN for advanced segmentation.
Traffic Monitoring and Analysis
The environment integrates professional network analysis tools. Wireshark enables detailed packet capture and analysis between segments, tcpdump facilitates programmatic capture for automated analysis, ntopng provides real-time flow monitoring, and Nagios or Zabbix can be implemented for proactive service monitoring.
Security Incident Simulation
Administrators can execute controlled red team/blue team exercises, implement honeypots with Cowrie or Dionaea for attack studies, simulate lateral movement between network segments, and practice incident response with forensic tools like Volatility for memory analysis.
Technical Specifications and Requirements
Host System Requirements
For optimal performance, the host system should have at least 8 GB of RAM (16 GB recommended for complex scenarios), processor with hardware virtualization support (Intel VT-x with EPT or AMD-V with RVI), 20 GB of free disk space for complete installation and expansion, and network card with promiscuous mode capability for advanced traffic analysis.
Hypervisor Compatibility
VMware: Compatible with Workstation Pro 15+, vSphere 6.7+, and Fusion 11+. Requires enabling nested virtualization (VT-x/AMD-V passthrough) and at least 4 vCPUs assigned to the host virtual machine.
KVM/Libvirt: Optimized for enterprise Linux distributions (RHEL 8+, Ubuntu 20.04 LTS+, SLES 15+). Uses QEMU 4.0+ with KVM acceleration and nested virtualization support enabled in the kernel.
Advanced Configurations and Customization
Laboratory Expansion
Experienced administrators can extend base functionality by adding new virtual machines through libvirt XML definitions, implementing additional services like Active Directory with Samba4, deploying distributed storage solutions with GlusterFS or Ceph, and integrating orchestration tools like Ansible for configuration automation.
Integration with Existing Infrastructure
NETinVM can integrate with development environments through bridge connections to physical networks, synchronization with Git repositories for configuration versioning, integration with CI/CD systems for automated network change testing, and connection to centralized logging platforms like ELK Stack.
Performance Optimizations
To maximize performance in educational production environments, it’s recommended to enable KSM (Kernel Same-page Merging) for memory optimization, configure CPU affinity to distribute load across physical cores, use SSD storage with thin provisioning for better I/O, and implement accelerated networking with SR-IOV when available.
Practical Laboratory Methodology
Network Configuration Exercises
Laboratories can include 802.1Q VLAN trunking implementation, spanning tree protocol configuration for redundancy, dynamic routing setup with OSPF or BGP, and load balancing implementation with HAProxy or nginx.
Troubleshooting Scenarios
Administrators can practice diagnosing connectivity issues using tools like mtr, traceroute, and advanced ping, performance problem analysis with iperf3 and nuttcp, DNS configuration debugging with dig and nslookup, and SSL certificate troubleshooting with openssl.
Automation and Scripting
The environment facilitates automation learning through Bash scripts for massive service configuration, Ansible playbook implementation for configuration management, Python usage with libraries like Netmiko for network automation, and custom monitoring script development.
Maintenance and Updates
Versioning and Backup
It’s recommended to implement backup strategies through virtual machine snapshots before critical changes, configuration versioning with Git, regular export of critical service configurations, and change documentation through ticketing systems or wikis.
Environment Updates
Updates should follow a controlled process including testing in isolated environment before production, complete backup of current state, gradual updating by services, and post-update functional validation through automated test suites.
Frequently Asked Questions for Administrators
How to configure nested virtualization on different hypervisors?
In VMware, nested virtualization requires enabling “Virtualize Intel VT-x/EPT or AMD-V/RVI” in the virtual machine configuration and ensuring the physical CPU supports these technologies. In KVM, you must load the kvm-intel module with “nested=1” or kvm-amd with “nested=1” depending on the processor, and verify with “cat /sys/module/kvm_intel/parameters/nested” that it returns “Y”. In enterprise environments with vSphere, you need to enable EVC (Enhanced vMotion Compatibility) in nested virtualization compatible mode.
What professional monitoring tools can be integrated with NETinVM?
NETinVM supports native integration with Prometheus for system and network metrics, Grafana for customizable visual dashboards, ELK Stack (Elasticsearch, Logstash, Kibana) for log aggregation and analysis, Zabbix for enterprise monitoring with advanced alerting, PRTG for hybrid on-premise/cloud monitoring, and SolarWinds for complex corporate environments. Integration is performed through SNMP agents, specific exporters, or RESTful APIs depending on the chosen tool.
How to implement high availability and clustering in the laboratory?
For high availability scenarios, multiple synchronized NETinVM instances can be configured through DRBD for block replication, implement clustering with Pacemaker and Corosync for automatic failover, configure load balancing with keepalived and VRRP for critical services, and use GlusterFS or Ceph for distributed storage. In more advanced environments, Kubernetes clustering can be implemented using kubeadm for container orchestration over the virtualized infrastructure.
What dynamic routing protocols can be practiced and how to configure them?
NETinVM supports complete implementation of enterprise routing protocols including OSPF with multiple areas and LSA types using Quagga or FRR, BGP for inter-AS routing with routing policies and path attributes, RIP for simple networks with hop count metrics, and EIGRP through open source implementations. Configuration is performed through vtysh for a Cisco-like experience, allowing practice of route redistribution, route filtering with route-maps, and convergence optimization with adjustable timers. For advanced scenarios, MPLS VPNs and segment routing can be implemented with SDN controllers like OpenDaylight.

