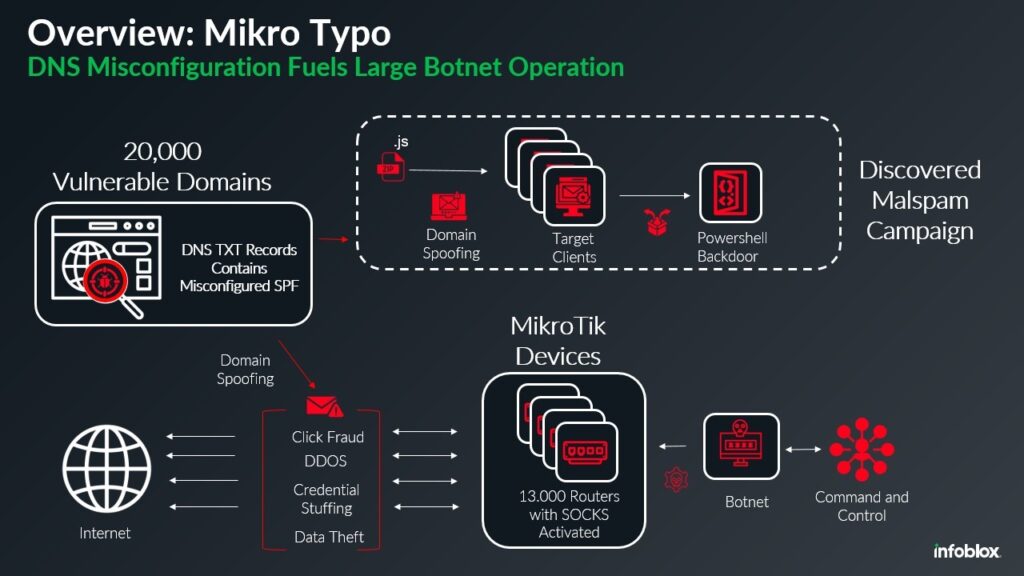
A botnet comprising 13,000 MikroTik devices has been identified exploiting misconfigurations in Sender Policy Framework (SPF) DNS records. This vulnerability allows attackers to bypass email protections and distribute malware by spoofing 20,000 web domains, according to DNS security firm Infoblox.
How the Attack Works
The attack leverages SPF records configured with the overly permissive “+all” setting, which allows any server to send emails on behalf of a domain. This misconfiguration effectively negates the purpose of SPF, which is to restrict email-sending to authorized servers using the safer “-all” option.
Infoblox detected this activity during a malspam campaign active in late November 2024. Some of the emails impersonated companies like DHL Express, including fake invoices in ZIP files containing malicious JavaScript payloads. Once opened, the script executed PowerShell commands to connect to a command-and-control (C2) server associated with Russian hacking groups.
Impact and Reach of the Botnet
The MikroTik botnet is configured as SOCKS4 proxies, significantly amplifying its impact and enabling it to anonymize malicious activities. Key functionalities include:
- DDoS Attacks: These devices have been previously implicated in large-scale attacks, such as a record-breaking 840 million packets-per-second attack last summer.
- Email Spoofing: Sending spam and phishing emails by impersonating legitimate domains.
- Data Exfiltration: Stealing sensitive data from compromised systems.
- Traffic Masking: Acting as intermediaries to conceal the real origin of malicious traffic.
Infoblox warns that, while the botnet contains 13,000 devices, its configuration as proxies allows hundreds of thousands of compromised devices to use it for network access, exponentially increasing its operational scale and impact.
MikroTik Vulnerabilities
The exact method of compromise remains unclear, but Infoblox observed that both older and newer MikroTik firmware versions are affected. MikroTik devices are popular for their power, but they are frequently targeted by attackers due to slow patch adoption among users.
Many devices remain vulnerable for extended periods because administrators fail to update firmware or apply proper configurations.
Mitigation Recommendations
To reduce risk, MikroTik device owners are strongly encouraged to take the following steps:
- Update firmware to the latest version available for their device.
- Change default admin credentials to a secure alternative.
- Disable remote access to management interfaces unless necessary.
- Review SPF records for their domains and replace “+all” with “-all” to prevent unauthorized email use.
Conclusion
This MikroTik botnet highlights the critical need for regular updates and proper configuration of network devices. With the rise of botnets leveraging such vulnerabilities, it’s essential for organizations and individual users to follow best practices to protect themselves from these evolving threats.
source: Administración de sistemas

