When your day swings between DNS changes, propagation windows, bouncing mail, and quirky CDNs, a lookup tool that hits authoritative name servers, travels over DNS over HTTPS (DoH), and leaves shareable evidence saves hours. NSLookup.Network is precisely that—a free, web-based nslookup that:
- Runs every query over DoH (HTTPS 443, encrypted).
- Queries the domain’s authoritative servers (not an arbitrary recursive).
- Normalizes inputs (FQDN, class IN, sane parsing).
- Surfaces TTL, authoritative source, and a timestamp for each answer.
- Lets you force “live” (authoritative) and compare cache vs. live.
- Emits a permalink for each result (ideal for tickets, postmortems, audits).
Below is a technical guide mapped to real sysadmin workflows.
1) Resolution model: why “authoritative + DoH” matters
Authoritative vs. recursive.
Recursors can serve cached data until TTL expiry; during migrations or flaky incidents, cache hides the truth. Authoritatives are the source of truth—what they answer is what the Internet will see after propagation.
DoH.
Queries travel via HTTPS (443), encrypted, dodging port-53 blocks, trivial MITM, and resolver fingerprinting. Handy on client networks with strict ACLs or inspection.
Normalization.
The tool canonicalizes the name (FQDN, trailing dot as needed), sanitizes inputs, and uses class IN. Fewer false negatives from casing or partial labels.
2) Record coverage (and what to check)
| Type | Purpose | What to verify |
|---|---|---|
| A / AAAA | IPv4/IPv6 for frontends | Expected IP; sane TTL; CNAME chain if present; authoritative consistency |
| MX | Inbound mail routing | Priorities; MX targets with direct A/AAAA (no CNAME); TTL |
| TXT (SPF/DKIM/DMARC, verifications) | Mail auth / service verification | SPF ≤ 10 lookups; valid DKIM selector/key; DMARC policy (p=), rua/ruf, alignment |
| NS | Delegation | Correct NS FQDNs (no CNAME); provider mix; glue at registrar if needed |
| SOA | Start of Authority | Serial monotonic; refresh/retry/expire; plausible MNAME |
| PTR | Reverse DNS | PTR→FQDN is correct; FQDN resolves back to the same IP (coherence) |
Tip: before changes, save the permalink as baseline (timestamped).
3) Operational runbooks (step-by-step)
A. Nameserver migration (delegation change)
- Pre-cut: build zone at the new provider; import records.
- On NSLookup.Network: query NS and SOA in live mode. Note:
- NS list (exact FQDNs).
- SOA serial and MNAME.
- Validate the new NS answer authoritatively for critical A/AAAA/MX/TXT/SRV (use live).
- Flip delegation at the registrar (plus glue for vanity NS).
- Re-check NS/SOA until authoritatives show the new set.
- Monitor TTL on sensitive records; communicate real windows to stakeholders.
Watch for:
- SOA serial increasing post-change.
- NS correctness, no CNAME.
- Authoritative consistency (no diverging answers).
B. Mail incidents (bounces, greylisting, spam flags)
- MX (live): points to the right provider (no CNAME).
- SPF: syntax valid, ≤10 lookups (
a,mx,include,exists). Avoid circular includes. - DKIM:
selector._domainkeyTXT present; key current, ≥1024/2048 bits. - DMARC:
_dmarcTXT; policyp=(none/quarantine/reject),rua/rufcorrect. - PTR: outbound IP’s PTR → FQDN, and FQDN → same IP (coherent).
- TTL: long TXT/MX TTLs delay fixes; use live and compare with cache to confirm authority now reflects changes.
C. Frontend flaps (404/SSL warnings/host not found)
- A/AAAA (live): confirm expected edge/origin IP; account for CNAME (CDN).
- SOA: check serial and timers; desynced authoritatives explain divergent answers.
- NS: mixed delegations across providers often cause accidental split-horizon.
- TTL: large TTLs slow rollback; pre-lower before critical changes, then raise after stability.
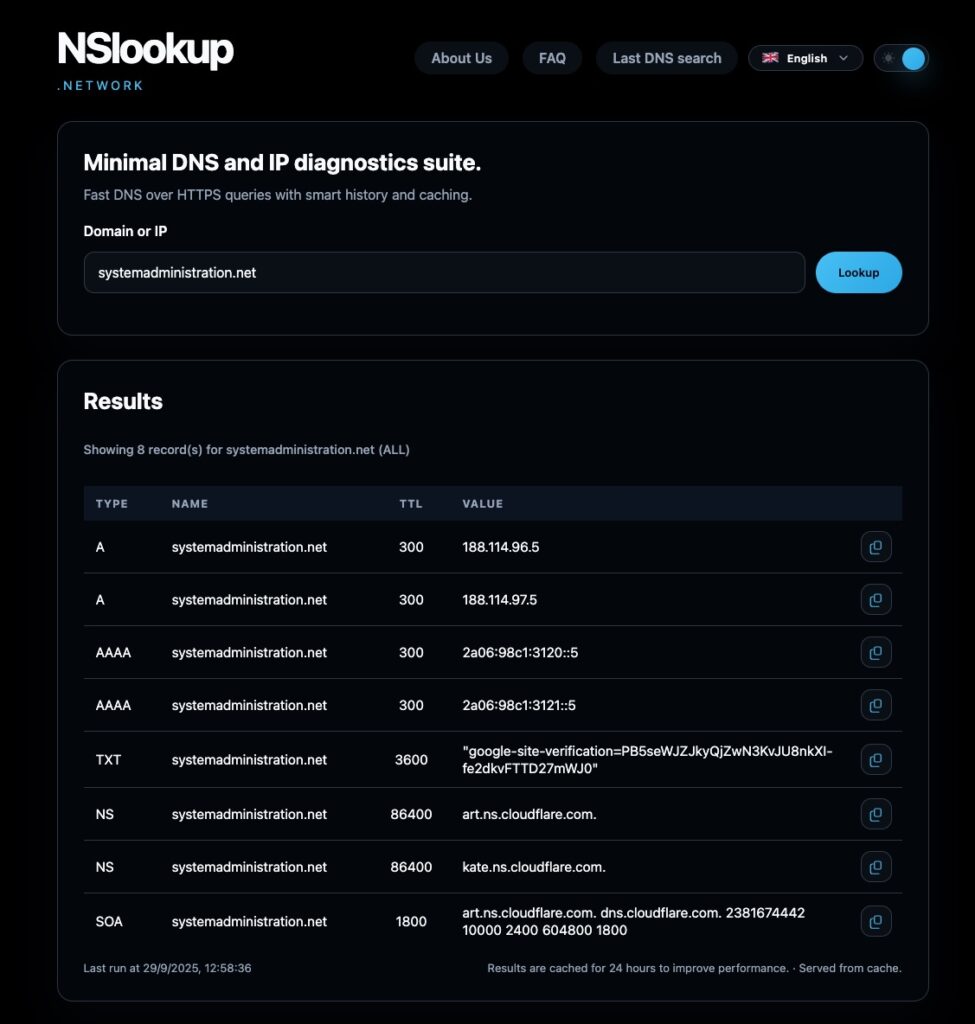
4) “Cache vs. Live”: when to use which
- Cache: fast repeats during bridges; contrast with live to avoid hammering auths.
- Live: whenever you need ground truth (migrations, fresh changes, divergences).
Typical patterns:
- Cache ≠ Live → Wait TTL, check SOA serial, verify from another network if you suspect intermediate recursors.
- Cache = Live but issue persists → Not propagation; investigate app, TLS, WAF/DNS firewall, or routing.
5) DNS ops best practices
- SOA serial discipline: always increase (e.g.,
YYYYMMDDnnor +1; never roll back). - TTL staging: lower TTL 24–48h ahead of big changes; raise after stabilization.
- No CNAME in MX: many MTAs reject it; RFC guidance prefers direct A/AAAA.
- Lean SPF: minimize
include; useip4/ip6where possible; stay under 10 lookups. - PTR coherence: essential for SMTP reputation.
- NS homogeneity: avoid mixing providers unless you control AXFR/IXFR and policies.
- Document with permalinks: paste lookup URLs into tickets/changelogs with UTC timestamps.
6) Common pitfalls (and fixes)
- Mistaking a recursive answer for authoritative → use Live, confirm NS/SOA.
- Leaving TTL at 86400 during urgent changes → do a pre-flight: lower TTL, change, test, then raise.
- MX pointing to CNAME → breaks delivery; use direct A/AAAA targets.
- SPF >10 lookups → silent
permerror; collapse ranges, trim includes. - Stale DKIM selector → rotate keys; watch
t=s/t=yflags in testing. - DMARC without
rua/ruf→ you lose telemetry to tune policy.
7) Workflow integration
- NOC/SOC: paste permalinks in alerts; compare cache vs. live to kill “DNS stale” theories early.
- DevOps/Platform: add SOA serial + NS (live) checks to deployment/migration runbooks.
- Marketing/SEO tech: verify campaign subdomains and TXT verifications via live; attach permalinks to tickets.
- Audit/compliance: rely on timestamps as evidence “before/after change”.
8) Task checklists
Frontend IP change
- Lower A/AAAA TTL.
- Apply change.
- A/AAAA live (auth source noted).
- Validate CNAME chain (CDN).
- Permalinks before/after.
Mail onboarding
- MX → provider (no CNAME).
- SPF valid (≤10 lookups).
- DKIM selector published.
- DMARC with sensible policy.
- PTR set for outbound IP.
Nameserver migration
- New zone loaded/validated.
- NS/SOA live (baseline).
- Flip delegation (+ glue if needed).
- NS/SOA live (post-flip).
- TTL windows communicated.
9) Privacy & safety
- DoH reduces metadata leakage and spoofing.
- Permalinks are great for evidence—avoid sharing internal hostnames/secrets in screenshots or links if the zone isn’t public.
- Don’t publish results for embargoed hostnames before go-live.
10) Limits & expectations
- NSLookup.Network does not change DNS, nor run 24/7 monitoring; it’s for lookup and evidence.
- It doesn’t replace
digfor deep DNSSEC/EDNS/trace scenarios, but it covers 80–90% of operational cases with better collaboration (permalinks, DoH, auth focus).
Bottom line
Sysadmins need to know what the Internet sees right now, prove it, and share it quickly. With authoritative DoH lookups, cache vs. live, visible TTL/serial, and permalinks, NSLookup.Network slots neatly into DNS, mail, and CDN runbooks—and cuts the time between “pager just went off” and “we have evidence-backed diagnosis.”
Technical quick FAQ
How do I measure real propagation?
Combine SOA serial + record TTL; compare cache vs. live; validate from another network if you suspect recursors holding TTL.
Can I detect split-horizon or desync?
Yes: NS (live) list, SOA serial, and A/AAAA (live). If auths differ among themselves, you have desync. If answers differ by client network, it might be split-horizon (by design) or a caching artifact.
Mail broken—what’s the order of checks?
- MX live, 2) SPF (≤10 lookups), 3) DKIM selector active, 4) DMARC, 5) PTR coherence, 6) TTL. Save permalinks to the ticket.
Does it help with DNSSEC?
It focuses on practical content/TTL/authority. For DNSSEC (AD flag, trust chain), use dig +dnssec/validators—then attach NSLookup.Network permalinks for the content/authority evidence.

