Trusted VMware utility used to spread information-stealing malware through spoofed domains and a brief compromise of the official website
RVTools, a widely trusted utility for gathering audit data from VMware vSphere environments, has become the center of a high-risk malware campaign. What makes this incident especially concerning for system administrators is that, for a limited time, even the official website served a malicious installer, not just impersonating domains.
Official Site Compromised: Malicious DLL Embedded in Installer
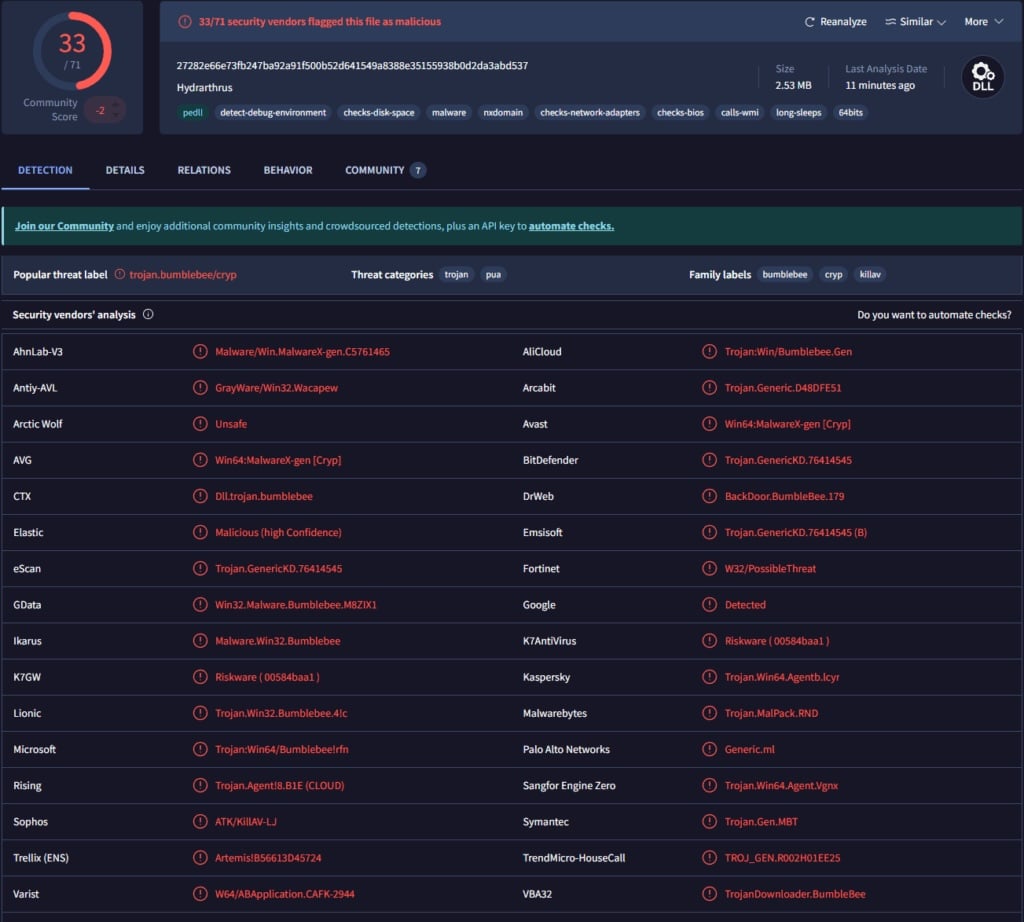
On May 13, 2025, security researcher Aidan Leon reported that Microsoft Defender for Endpoint triggered a high-confidence alert shortly after an employee downloaded RVTools from robware.net — the tool’s long-standing official site. The alert flagged a suspicious version.dll file within the installer’s directory, later identified as Bumblebee, a well-known malware loader often linked to ransomware operations and post-exploitation frameworks.
Leon confirmed the malicious installer was first submitted to VirusTotal on May 12, suggesting the compromise occurred that same morning. By Tuesday afternoon, the file had been replaced with a clean version, and the website was briefly restored. However, the site went offline again soon after.
Dell Responds: Denies Breach, Confirms DDoS and Lookalike Sites
Dell Technologies, which currently maintains RVTools, issued a statement denying a confirmed breach of their servers. However, they acknowledged denial-of-service (DDoS) attacks and the emergence of malicious copycat websites, some of which rank above the official site on search engines.
They emphasized that robware.net and rvtools.com are the only official download portals and urged users not to download the utility from any other source — even though both sites remain offline as of this writing.
Malware Capabilities and Admin Risk
The malicious installer is designed to execute alongside the legitimate tool, making it difficult to detect. Once installed, it enables attackers to:
- Extract system credentials and Windows secrets
- Harvest browser-stored passwords and crypto wallet data
- Collect sensitive files and configuration data
- Establish persistence for further exploitation
For VMware admins, this could result in the compromise of vCenter credentials, ESXi host access, datastore configurations, and virtual network settings — creating an ideal entry point for lateral movement and ransomware deployment.
Key Recommendations for System Administrators
- Always verify the download source: Use only robware.net or rvtools.com and avoid third-party or sponsored links in search results.
- Validate installer integrity: Check the SHA256 hash of the file against known good versions on VirusTotal or developer-released hashes.
- Apply endpoint protection policies: Use application control and allowlisting to prevent the execution of unauthorized binaries on administrator workstations.
- Limit admin privileges: Use non-privileged accounts for daily tasks and isolate critical vSphere access to secure jump hosts.
- Monitor for suspicious outbound traffic: Look for beaconing or unexpected DNS requests after RVTools installations.
Lessons for the Admin Community
The RVTools incident is a stark reminder that trusted tools are not immune to becoming attack vectors, especially in highly targeted environments like virtualization and infrastructure management. Administrators should treat every installer — even from known sources — with the same scrutiny as any potentially dangerous software.
Security hygiene practices such as hash verification, file reputation checks, and zero-trust principles must be applied consistently. In critical infrastructure, the margin for error is zero — and attackers are increasingly counting on complacency.
Reference: Revista Cloud, Zero day labs (img), Una al dia y Help net security