Starlink’s new “Community” service allows a single satellite terminal to be shared among multiple households. But to make this setup viable, admins must deploy proper network segmentation, traffic control, and secure isolation. Here’s how to architect it using VLANs, MikroTik, and OpenWRT.
Starlink’s new service model for residential communities represents a step forward in universal connectivity. The idea is simple: a single Starlink antenna provides service to multiple users in a building, each with their own account and isolated setup. However, to make this technically sound, a properly segmented infrastructure is required—ideally via VLANs.
Unlike traditional deployments with one CPE per user, this new approach is closer to what you’d see in community ISPs or campus-style networks. Choosing the right hardware, network design, and access control policies is crucial to avoid performance bottlenecks and security risks.
Physical and Logical Architecture
🔌 Typical Infrastructure:
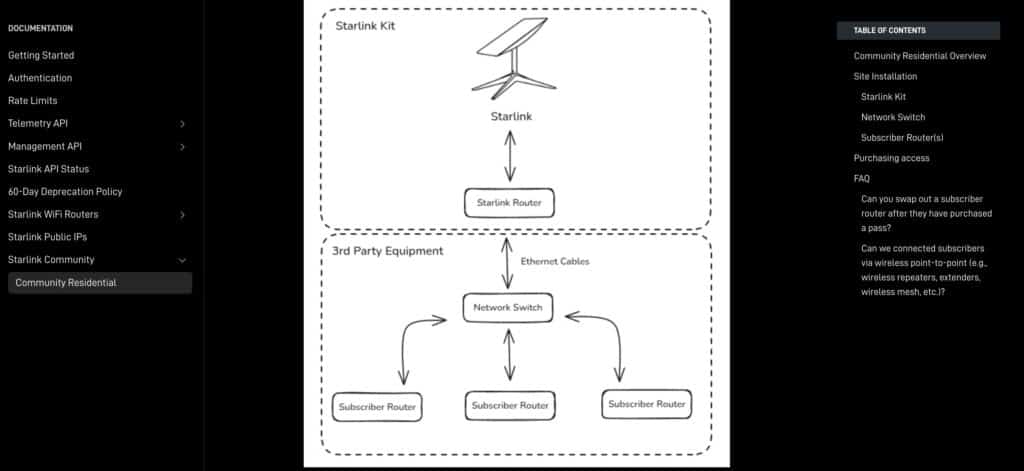
[Starlink Antenna] → [Starlink Router] → [802.1Q-enabled Switch] → [VLAN Segmentation] → [User Routers]
Code language: CSS (css)- Starlink Router serves as the internet gateway.
- Managed L2/L3 switch enforces VLAN segmentation per user.
- Customer Routers (CPEs) act as NAT firewalls and private Wi-Fi endpoints.
- Best practice: per-port VLAN tagging with dedicated subnets per user.
🧩 Recommended Hardware:
- MikroTik CRS3xx, RB5009, hEX S / hAP ac³
- OpenWRT-compatible: Linksys WRT series, GL.iNet, NanoPi R6S
- VLAN-capable switches: Netgear GS108Ev3, TP-Link TL-SG2008, Zyxel GS1900
VLAN Configuration (Per User)
MikroTik (RouterOS 7.x)
/interface vlan
add name=vlan10 vlan-id=10 interface=ether2
add name=vlan20 vlan-id=20 interface=ether3
/ip address
add address=192.168.10.1/24 interface=vlan10
add address=192.168.20.1/24 interface=vlan20
/ip dhcp-server
add interface=vlan10 lease-time=1h name=dhcp1
add interface=vlan20 lease-time=1h name=dhcp2
Code language: PHP (php)- NAT and firewall rules per subnet.
- Optional: traffic shaping using queues or simple queues.
OpenWRT (LuCI + UCI)
- Create logical VLAN interfaces (
eth0.10,eth0.20, etc.) - Assign each VLAN to a separate firewall zone.
- Enable
dnsmasqwith custom DHCP scopes. - Use SQM + CAKE for per-zone traffic management.
Best Practices and Design Notes
| Component | Technical Recommendation |
|---|---|
| IP addressing | Private subnet per VLAN (e.g. 192.168.X.0/24 per tenant) |
| DHCP | Isolated scope per VLAN |
| DNS | Optional DNS forwarders per VLAN |
| Inter-VLAN Firewall | Block all forwarding between VLANs |
| QoS | Use per-VLAN shaping (queues, SQM, CoDel, CAKE) |
| IPv6 | Disable unless controlled – may introduce privacy and routing issues |
| Logging | Use remote syslog by interface or zone |
Benefits of the VLAN-Based Architecture
- Administrative autonomy: each user manages their own router, SSID, LAN settings.
- Modular scalability: simply extend switch ports and assign new VLANs.
- Strong isolation: prevents ARP poisoning, traffic sniffing, and broadcast storms.
- Logical decoupling: users can use different OSes, DNS providers, or VPNs safely.
Technical Limitations and Risks
| Factor | Description |
|---|---|
| Shared Bandwidth | All users share the antenna’s bandwidth (e.g. 200 Mbps DL shared among tenants) |
| Latency | Varies with satellite load and weather (typically 40–120 ms) |
| No on-site support | Host is responsible for physical installation and basic maintenance |
| Single point of failure | Starlink router or switch going down affects all users |
| Physical security | Central gear (router/switch) should be locked or access-controlled |
Legal & Commercial Notes
- Each tenant has a direct contract with Starlink.
- This is not resale: the “host” only manages hardware and onboarding.
- May require rooftop access or community approval in shared buildings.
Ideal Use Cases
- Rural or peri-urban areas lacking FTTH.
- Old buildings with no internal telecom infrastructure.
- Temporary or pop-up locations (e.g. campuses, construction sites).
- Small apartment buildings seeking backup connectivity.
Technical FAQ
Can I prioritize specific VLANs or services?
Yes, using MikroTik queues or OpenWRT SQM with DSCP classification.
Can I run OSPF/BGP in this setup?
Possible but overkill. Static routing with NAT is more suitable in most cases.
How secure is this configuration?
With VLANs and per-zone firewalls, isolation is strong. Auditing configs is recommended.
Can I mix in VoIP or IPTV services?
Yes, but they should run in separate VLANs with proper QoS (voice VLANs, multicast config).
Should I enable IPv6?
Not unless strictly managed. Stateless addressing and privacy extensions complicate logging and access control.

