SUSE is redefining enterprise cybersecurity with its comprehensive Zero Trust Infrastructure strategy, moving far beyond traditional network and access controls. In a rapidly evolving threat landscape and under increasing regulatory pressure, SUSE’s approach secures not only access points but also workload execution and infrastructure integrity — from cloud to edge.
Zero Trust Infrastructure: Beyond Access Control
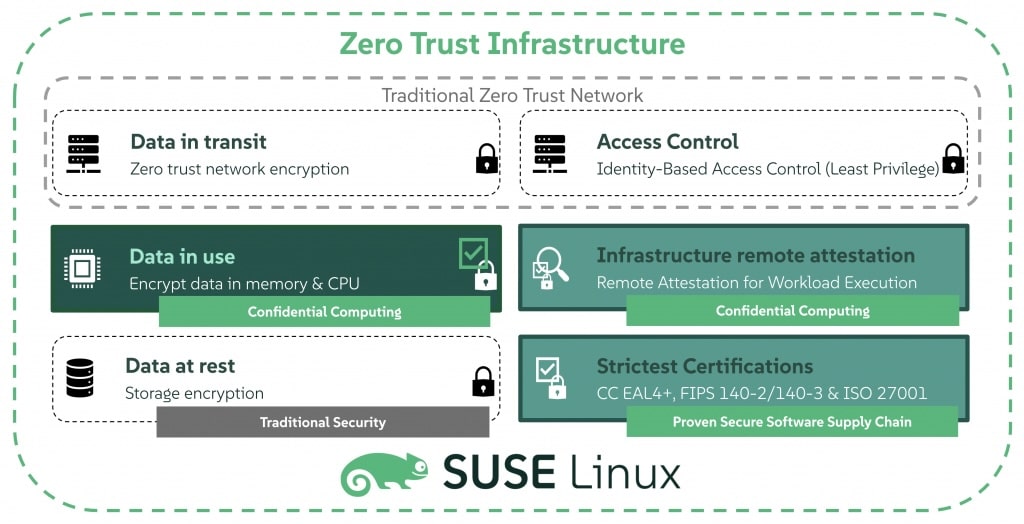
While Zero Trust was once limited to identity management and network security, modern threats demand a broader scope. SUSE’s Zero Trust Infrastructure ensures sensitive workloads execute in verified, encrypted environments. This means eliminating implicit trust in cloud providers, host operating systems, or even privileged administrators — a critical step in protecting against insider threats and supply chain attacks.
Why Enterprises Need Zero Trust for Workload Execution
With Confidential Computing as a key component, SUSE’s Zero Trust Infrastructure offers organizations multiple advantages:
- Mitigation of insider and cloud risks: Prevents unauthorized access to workloads, even by administrators or infrastructure providers.
- Guaranteed workload integrity: Ensures applications run only in verified, isolated execution environments.
- Protection of confidential data: Encrypted memory keeps sensitive information secure during processing.
- Simplified compliance: Supports regulatory demands in sectors like finance, government, and healthcare through hardware-backed security.
- Verifiable attestation: Provides concrete proof that workloads are running in secure environments, crucial for audit readiness.
Remote Attestation: The Compliance Backbone
One of the biggest gaps in traditional cloud security is the absence of verifiable evidence that sensitive data is processed securely. SUSE addresses this challenge with robust remote attestation capabilities, ensuring:
- Only verified, Confidential Computing-enabled workloads are executed.
- Continuous evidence is available to demonstrate compliance for audits or investigations.
- Integrated vulnerability management and policy enforcement across the entire infrastructure.
This level of transparency is increasingly vital in meeting regulatory standards like GDPR, NIS2, and DORA.
SUSE’s Two-Pillar Security Foundation
SUSE’s approach to Zero Trust Infrastructure is built on two critical pillars:
1. A Certification-Validated Secure Software Supply Chain
SUSE stands apart by offering a supply chain validated to Common Criteria EAL4+ certification — a requirement for government and highly regulated industries. This reduces enterprise liability and simplifies compliance audits by providing provable trust in every component of the operating system.
2. Confidential Computing for Secure Workload Isolation
Confidential Computing extends Zero Trust principles into the runtime environment, using hardware-backed memory encryption and attestation to protect sensitive data from insider threats, compromised hypervisors, and malicious infrastructure providers.
Real-World Deployment: Defense and Government Use Cases
In defense and government, physical security is no longer enough. Infrastructure can be compromised through insider access or unauthorized tampering. SUSE’s Zero Trust Infrastructure, combining KVM-based isolation and Confidential Computing, enables mission-critical workloads to execute securely, even in environments with limited physical control.
For example, a defense agency leveraged SUSE Linux’s Confidential Computing features to:
- Encrypt memory, making data extraction impossible even with physical hardware access.
- Continuously verify workload integrity through remote attestation.
- Eliminate trust dependencies on third-party infrastructure providers, safeguarding against espionage and insider manipulation.
Scaling Zero Trust Across Clouds and Edge
SUSE Linux Enterprise Server, with support for host and guest Confidential Computing and pre-built images for major hyperscalers, allows organizations to extend Zero Trust security policies across any environment — whether on-premises, in multi-cloud deployments, or at the edge.
With SUSE Multi-Linux Manager’s attestation capabilities, organizations can monitor, enforce, and prove security compliance across their entire digital infrastructure.
Redefining Trust in Infrastructure
SUSE’s strategy moves beyond traditional trust models to create a truly secure environment where every layer — from the operating system to workload execution — is verified and protected. With continuous innovation, strict security certifications, and robust supply chain validation, SUSE Linux stands as the trusted OS foundation for enterprises aiming to implement Zero Trust Infrastructure at scale.
In today’s world, where cybersecurity risks grow more sophisticated by the day, SUSE provides the critical assurance that enterprises need to protect sensitive workloads, meet regulatory demands, and operate with confidence across every environment.
Source: Suse

