Recent findings at the UK’s National Museum of Computing have reignited fears about the so-called Year 2038 Problem — often nicknamed the “Epochalypse.” While experts have long warned about the risk of a digital breakdown on January 19, 2038, new evidence suggests that some vulnerable systems may begin to fail a year earlier, in 2037.
A déjà vu of Y2K, but far more complex
Back in 1999, the world scrambled to prepare for the “Y2K bug,” a flaw in which dates were stored using only two digits for the year. Many feared computers would interpret the year 2000 as 1900, leading to global chaos. The crisis was largely averted thanks to widespread remediation efforts.
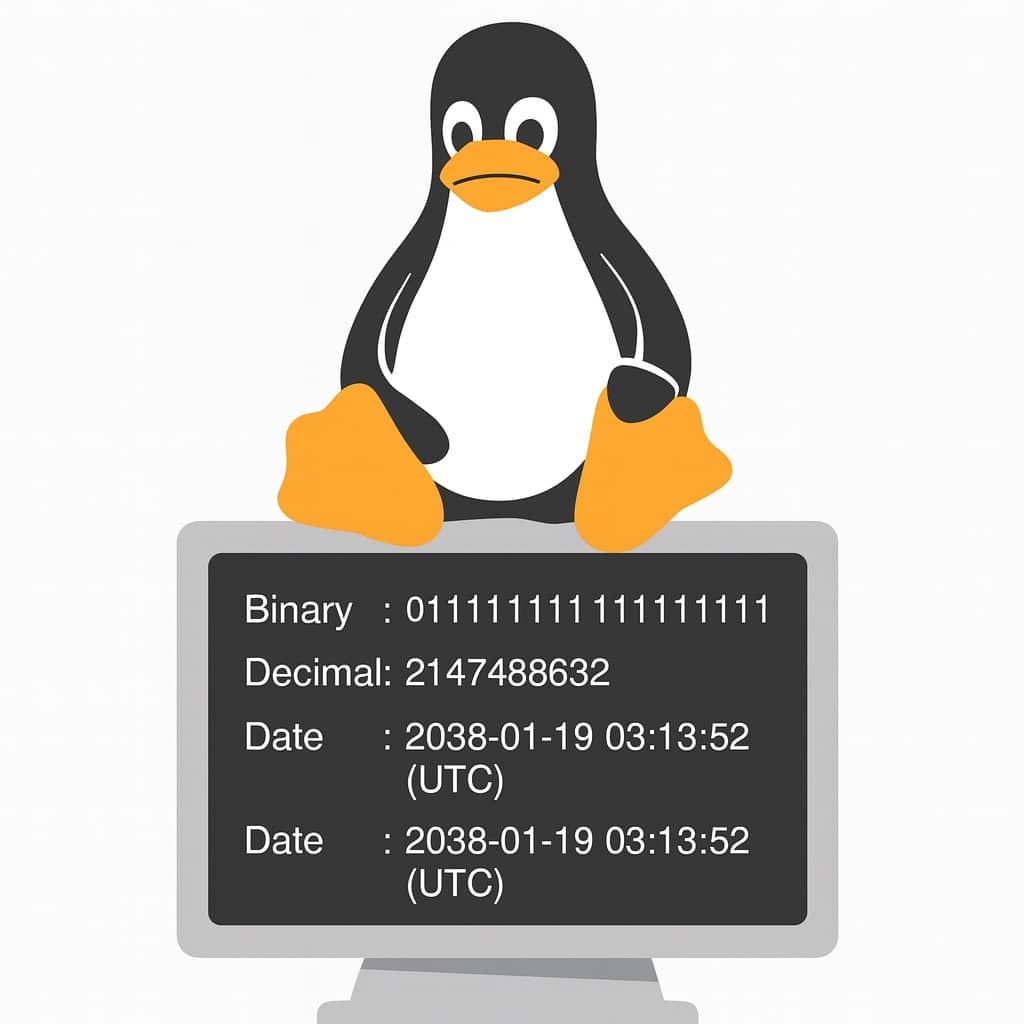
The Year 2038 Problem is similar in spirit but far more technical — and potentially trickier to solve. Instead of affecting how applications display dates, it’s rooted in how Unix-based systems, including Linux, actually store and calculate time.
Unix time counts the seconds since January 1, 1970 (UTC), using a signed 32-bit integer (time_t). That integer will reach its maximum value at 03:14:07 UTC on January 19, 2038. Just one second later, the counter will overflow, rolling over into negative territory and producing absurd results, like 1901 or 1970.
Unlike Y2K, which hit uniformly, the 2038 bug manifests differently depending on the compiler, the C libraries, and the hardware architecture in question. This unevenness makes it much harder to predict — and therefore harder to fix across the board.
A disturbing early failure: the 2037 bug on a PDP-11
The alarm was raised during restoration of a vintage PDP-11/73 computer. When engineers set the system clock forward to 2037, a year before the official rollover date, they discovered that the C library function time_t() crashed unexpectedly.
The hardware clock kept time correctly, but software calls failed, returning invalid dates or freezing entirely. The problem stemmed from the PDP’s 1982 C compiler and its libc implementation, which had not been designed to anticipate this edge case.
Robin Downs, a museum volunteer and veteran systems expert, put it bluntly:
“We found bugs that show up even before 2038 — vulnerabilities we didn’t know existed.”
While this doesn’t mean Linux or modern Unix will necessarily fail in 2037, it proves the point: different systems may break at different times, and not all failures will wait until the infamous rollover moment.
Linux and the countdown to 2038
Most modern Linux systems running on 64-bit architectures are immune. That’s because time_t is 64 bits wide on such systems, capable of representing dates billions of years into the future.
The danger lies with 32-bit systems, many of which still run in embedded devices, routers, industrial controllers, and older Android smartphones. On those, time_t is still a signed 32-bit integer — and will overflow in 2038.
The Linux kernel addressed this in version 5.6 (2020), adding support for 64-bit time_t even on 32-bit architectures. The GNU C Library (glibc) followed suit in version 2.34 (2021), allowing developers to compile applications with _TIME_BITS=64. This means that properly updated Linux distributions can survive beyond 2038 — but only if all dependent software is recompiled or adapted. If not, vulnerable binaries will continue to misbehave despite the kernel’s safeguards.
Debian, among other Linux distributions, has already begun migrating to 64-bit time support, but the process is complex and requires careful coordination (The Register).
Legacy systems: the real ticking time bomb
The real concern lies outside modern servers and desktops. Countless embedded systems — from banking infrastructure to telecom switches, medical equipment, industrial robots, and even cars — still run on outdated hardware and software. Many of these devices are expected to operate for decades without updates.
When the epoch rollover hits, or even before, those systems may:
- Misreport time and dates,
- Corrupt logs and transactions,
- Crash critical processes, or
- Render devices completely unusable.
As Robin Downs warned:
“We’re building devices and software today that we expect to last 12 or more years — but not all are ready for this contingency.”
Why 2038 may be worse than Y2K
The Y2K bug was predictable and relatively uniform — two digits became four. The 2038 issue is messier. Different compilers, libraries, and operating systems may react in wildly different ways to the overflow.
That unpredictability makes testing and remediation harder. Without a universal fix, every device and every software package needs to be individually checked and updated.
And as the PDP-11 test shows, failures may not all occur on the same date. Some systems could start misbehaving in 2037, making this bug a moving target rather than a single “event day.”
Conclusion
The Year 2038 Problem is not a distant theoretical threat — it’s a looming challenge. Linux and other modern 64-bit systems are safe, but billions of embedded and legacy devices are not. The discovery that some systems may begin to fail in 2037 only raises the urgency.
With just over 12 years left, the world must take this seriously — not repeat the complacency of assuming that “someone else will fix it.” Unlike Y2K, this bug will not strike uniformly, but in scattered, unpredictable ways, making preparation more difficult.
The time to act is now.
FAQ: Understanding the Year 2038 Problem
1. What exactly is the Year 2038 Problem?
It’s a bug in Unix-like systems that use a signed 32-bit integer (time_t) to store time as seconds since January 1, 1970. On January 19, 2038, the counter overflows, flipping into negative values and causing dates to appear as 1901 or 1970.
2. Why might the bug appear in 2037?
Tests on a vintage PDP-11 showed failures in 2037 due to how its 1980s compiler handled time_t. While this doesn’t apply to modern Linux, it demonstrates that not all systems will fail at the same moment. Some may experience errors earlier, depending on implementation quirks.
3. Is Linux safe from the 2038 bug?
Modern 64-bit Linux systems are safe, since time_t is 64 bits wide. Since Linux kernel 5.6 (2020) and glibc 2.34 (2021), even 32-bit systems can support 64-bit time_t, provided applications are recompiled. The real danger lies in unmaintained 32-bit devices.
4. Which systems are most at risk?
Legacy systems and embedded devices — like older Android phones, industrial machinery, medical devices, and infrastructure hardware. Many of these cannot or will not be updated, making them the most likely to fail.
5. How is this different from Y2K?
Y2K was uniform and predictable: two-digit years became four. The 2038 bug is fragmented, inconsistent, and may show up differently depending on hardware, compilers, or libraries. This makes it more unpredictable and harder to fix universally.