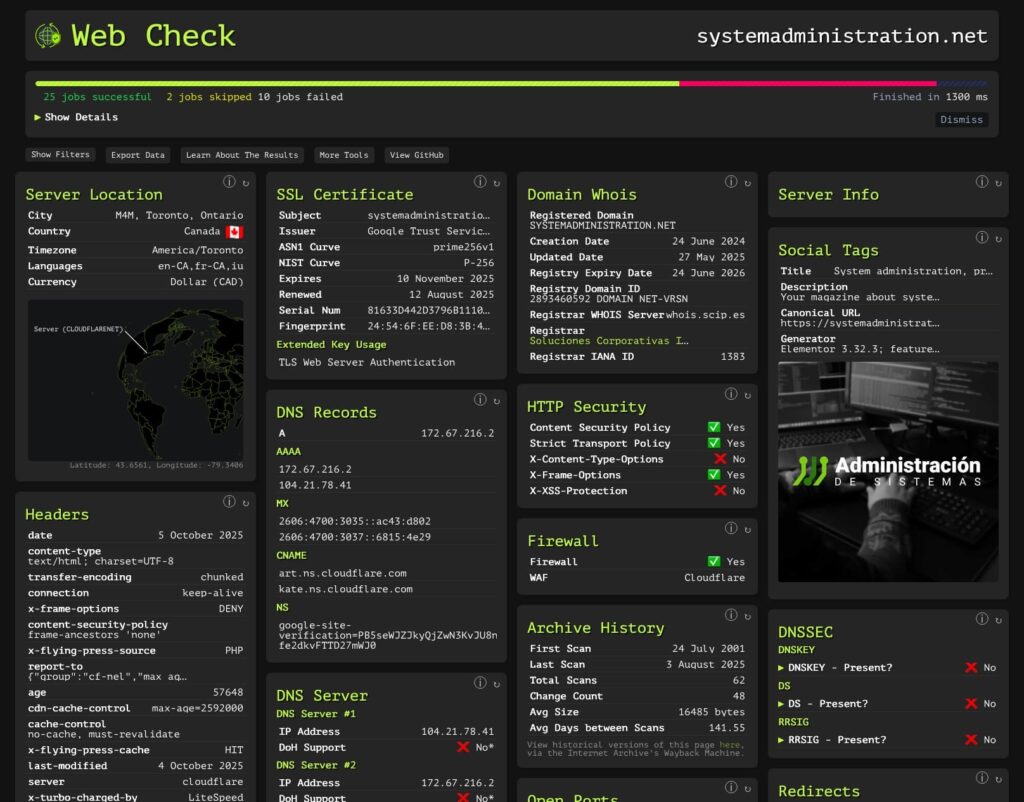
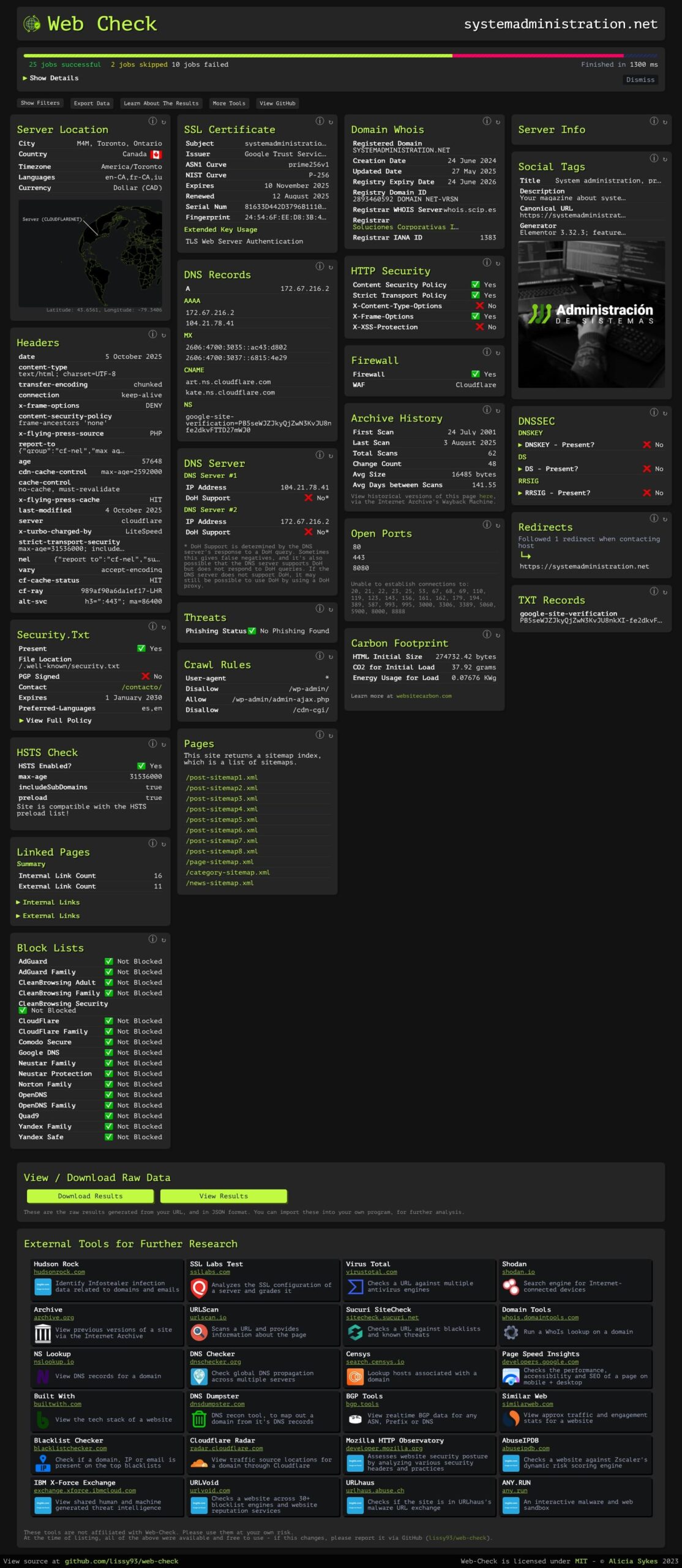
What it is. Web-Check is a 100% open-source tool that performs on-demand, comprehensive OSINT on any website. In about 20 seconds, it shows a dashboard with 30+ checks across security, architecture, and public footprint: from IP, DNS, and SSL chain to HTTP headers, cookies, open ports, TLS, DNSSEC, trackers, redirects, and sitemap/robots, plus practical extras like traceroute, server location, global rank, and carbon footprint. The project is authored by Alicia Sykes (Lissy93), licensed under MIT, and offered free with a hosted instance, a self-host option (Docker, Vercel, Netlify), and an API.
What it checks (and why it matters)
The dashboard aggregates everything into a single view so any role—devs, SecOps, SEO, or admins—can spot weak configs, attack vectors, and optimization opportunities:
- Identity & perimeter: IP, Whois/Domain info, DNS (A/AAAA, CNAME, NS, MX, TXT), DNSSEC, DNS servers, associated hostnames.
- TLS/HTTP layer: SSL chain, TLS version/cipher suites, HSTS, security headers (CSP, X-Frame-Options, X-Content-Type-Options, Referrer-Policy…), cookies (Secure/HttpOnly/SameSite), TLS handshake simulation.
- Exposure & attack surface: open ports, traceroute, firewall/WAF detection, malware & phishing checks, block-list checks.
- Crawl & content: robots.txt, sitemap / listed pages, linked pages, crawl rules, security.txt, social/open-graph tags.
- Performance/UX: quality metrics, headers/cache, redirect chain, status/uptime (when configured).
- Tech & footprint: detected tech stack (frameworks, CDN, WAF, analytics), global ranking, carbon footprint estimate.
- Visual extra: site screenshot for quick auditing and record-keeping.
The philosophy is simple: put in one click what an attacker could already find across scattered tools. For blue teams it’s an actionable checklist; for devs, a technical snapshot to speed up hardening and debugging; for product/SEO, indexing and social metadata signals.
How to use it
- Public instance: go to web-check.xyz, enter a URL, and get the report. No signup; no config required.
- API: consume endpoints to automate checks and plug Web-Check into CI/CD, security inventories, or lightweight cron monitors.
- Self-host: clone the repo and deploy via Docker or Vercel/Netlify. Defaults work without keys, but env vars unlock extra checks or higher rate limits for third-party APIs (some jobs rely on external services).
Optional requirements: certain checks—traceroute, advanced DNS resolution, or headless screenshot—need chromium, traceroute, and DNS utilities installed. If missing, those jobs are skipped automatically.
Privacy & operational security
- No accounts, no intrusive telemetry.
- Client-side keys (REACT_APP_*) must be minimally scoped, since they can be observed in browser↔server traffic.
- Checks using third-party APIs respect quotas; bring your own key if you want dedicated rate limits.
- The code is open (MIT), so you can audit how data is processed.
Quick use cases (checklists)
1) Security quick-scan before a release
- TLS ≥ 1.2, HSTS on, CSP without dangerous wildcards, cookies with Secure/HttpOnly/SameSite, anti-MIME/XSS/framing headers.
- DNSSEC where appropriate, MX and SPF/DKIM/DMARC aligned.
- Open ports: only intended services; no forgotten panels.
- WAF detected; clean redirects (no long chains).
2) Post-migration sanity
- Resolved IP and ASN correct, valid TLS, coherent redirect chains, robots/sitemap updated, social tags on key pages.
- Traceroute and latency acceptable; CDN caching applied.
3) Third-party/vendor audit
- Which tech do they use? Do they have security headers? Are certs and ciphers modern?
- Any block-list or malware/phishing flags?
- Which subdomains and ports are exposed?
4) Green IT & comms
- Carbon estimate + performance/quality feed your sustainability narrative and efficiency roadmap.
Self-hosting in 3 steps
- Clone:
git clone https://github.com/Lissy93/web-check && cd web-check - Install: Node ≥ 18.16.1, yarn, and optionally chromium/traceroute/dnsutils
- Run:
yarn && yarn start(or build a Docker image and pass envs with--env)
On Vercel/Netlify, add env vars in the UI to enable optional jobs or higher rate limits.
Contribute (or sponsor)
PRs are very welcome—new checks, UX refinements, refactors, docs, translations. For bug reports, include repro steps, logs, and environment. If you rely on the hosted instance, sponsorship helps cover costs (the serverless usage is about $25/month), keeping Web-Check free for everyone.
What sets it apart from other OSINT toolboxes
- All-in-one: 30+ signals in one coherent view—no need to stitch scripts and sites.
- Usability: clear report for non-pure-security roles (dev, PM, SEO) with immediate action.
- Portability: hosted, on-prem, or at the edge, with an API for pipelines.
- MIT License: minimal legal friction for companies and education.
Roadmap (per the repo)
The “official” job list lags what’s already in main—the author notes “many more have been added”—and promises new checks and UI improvements. Given the PR pace, expect new modules (e.g., deeper CSP analysis, policy linting, or Core Web Vitals with field data where keys are provided).
FAQ
Do I need keys to use Web-Check?
Not for the basics. Some checks use external APIs with quotas; add your env vars for higher rate limits or enhanced results.
Is it “safe” to analyze my domain?
It uses OSINT (non-intrusive) techniques. Still, review the code and, if preferred, self-host in your own network. Jobs needing system tools are skipped if unavailable.
Can I plug it into CI/CD?
Yes. Use the API to get a JSON report and fail builds if headers/HSTS are missing, TLS is outdated, etc. You can also archive screenshots and artifacts per commit.
What if a job fails in my environment?
It’s marked skipped. Install chromium, traceroute, or DNS utilities to enable those checks. Check server logs for details.
Links: source & README at github.com/Lissy93/web-check · public instance: web-check.xyz.