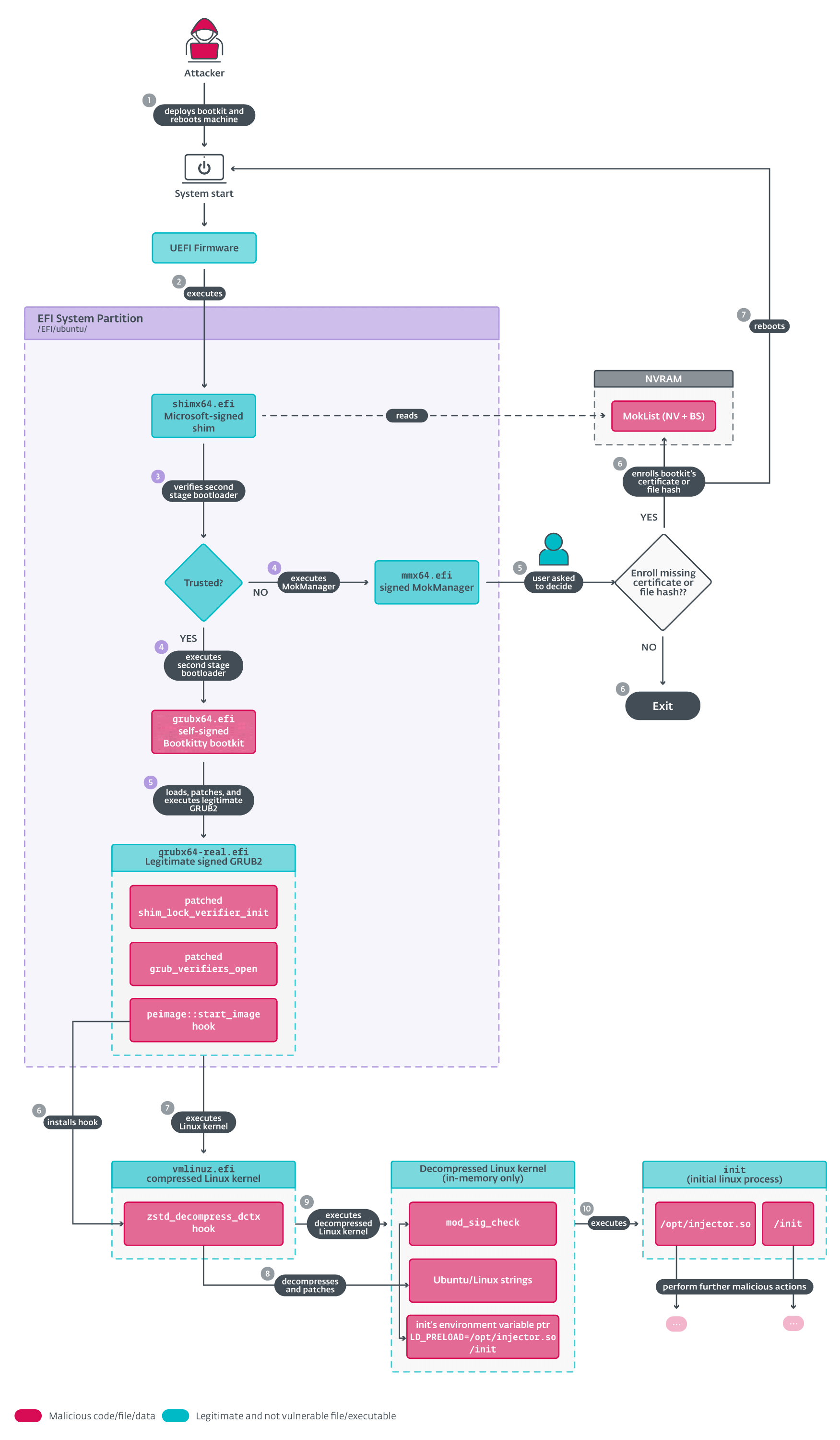
Researchers from the security firm ESET have identified the first UEFI bootkit specifically designed for Linux systems. This discovery, named Bootkitty, marks a turning point in firmware-related threats, as such attacks had previously targeted only Windows systems.
A Prototype with Limitations, Yet Significant
According to ESET’s analysis, Bootkitty appears to be a prototype or proof of concept rather than a fully operational threat. Its infection capability is limited to certain versions of Ubuntu, one of the most popular Linux distributions, and it lacks mechanisms to infect other Linux variants. Additionally, it exhibits significant flaws in its functionality, including errors in how it modifies the Linux kernel, which can cause system crashes instead of compromising them.
The bootkit fails to bypass the UEFI Secure Boot defense system, a measure that uses cryptographic signatures to ensure that each component loaded during boot is verified and approved by the device manufacturer. This significantly reduces infection opportunities on systems with Secure Boot enabled.
A Shift in the UEFI Threat Landscape
Despite its limitations, Bootkitty represents a concerning shift in the cybersecurity landscape. According to ESET researchers, “Bootkitty breaks the belief that modern UEFI bootkits are Windows-exclusive threats.” While the current prototype does not pose an immediate danger to most Linux systems, its development suggests that malicious actors are investing resources into creating tools of this kind for Linux.
Bootkitty’s Functionality and Vulnerabilities
The bootkit’s operation involves the following key steps:
- Execution of the bootkit and patching of the GRUB bootloader.
- Modification of the Linux kernel’s EFI loader.
- Alteration of the decompressed Linux kernel image.
One of its biggest shortcomings lies in its lack of kernel version checks, which can result in applying incorrect patches to system code, leading to fatal errors. Additionally, it leaves noticeable traces that make it easier to detect, undermining one of the main advantages of bootkits: stealth.
Preparing for Future Threats
While Bootkitty does not pose an immediate and effective threat, its emergence highlights the need to be prepared for future, more sophisticated developments. As ESET explains, this discovery underscores the importance of strengthening the security of Linux systems against potential advances in this type of malware.
The finding also emphasizes the necessity of wider adoption of measures like Secure Boot, along with the development of more effective tools to detect and mitigate firmware-based threats.
A Wake-Up Call for the Linux Community
The Linux community, historically perceived as less vulnerable to cyber threats compared to Windows, must remain vigilant about these developments. Although Linux remains more secure in many respects, its growing adoption in enterprise and server environments makes it an increasingly attractive target for cybercriminals.
Bootkitty, though limited, serves as a reminder that no system is completely immune. Preparation, constant software updates, and strengthening boot-level defenses will be essential to mitigate future threats.

