Strong Password Day 2025: Beyond Just Changing Passwords
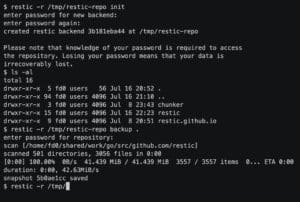
Since its creation in 2012, Change Your Password Day has served as an annual reminder of the importance of updating access credentials to protect digital security. However, cybersecurity experts have