In a world where email easily devours the workday, Inbox Zero arrives with a clear proposition: an AI-powered personal assistant for email, open source and self-hostable, that organizes the inbox, pre-drafts replies in the user’s tone, and tracks follow-ups so nothing slips through the cracks. The project can be deployed on Vercel or on a Docker-based VPS, and positions itself as a customizable alternative to closed, vendor-hosted services—without compromising security or ownership.
The stated mission is simple: spend less time in the inbox, more time on what matters. To get there, the app combines intelligent automation, plain-English rules, and a modern interface built with Next.js, Tailwind CSS, shadcn/ui, Prisma, Upstash, and Turborepo. From first contact, it reads like a product for demanding users—especially professionals and technical teams—who value control and privacy over the convenience of yet another opaque cloud.
A 24/7 assistant that understands context
Inbox Zero’s core revolves around a set of practical features aimed at reducing cognitive overhead and decision fatigue:
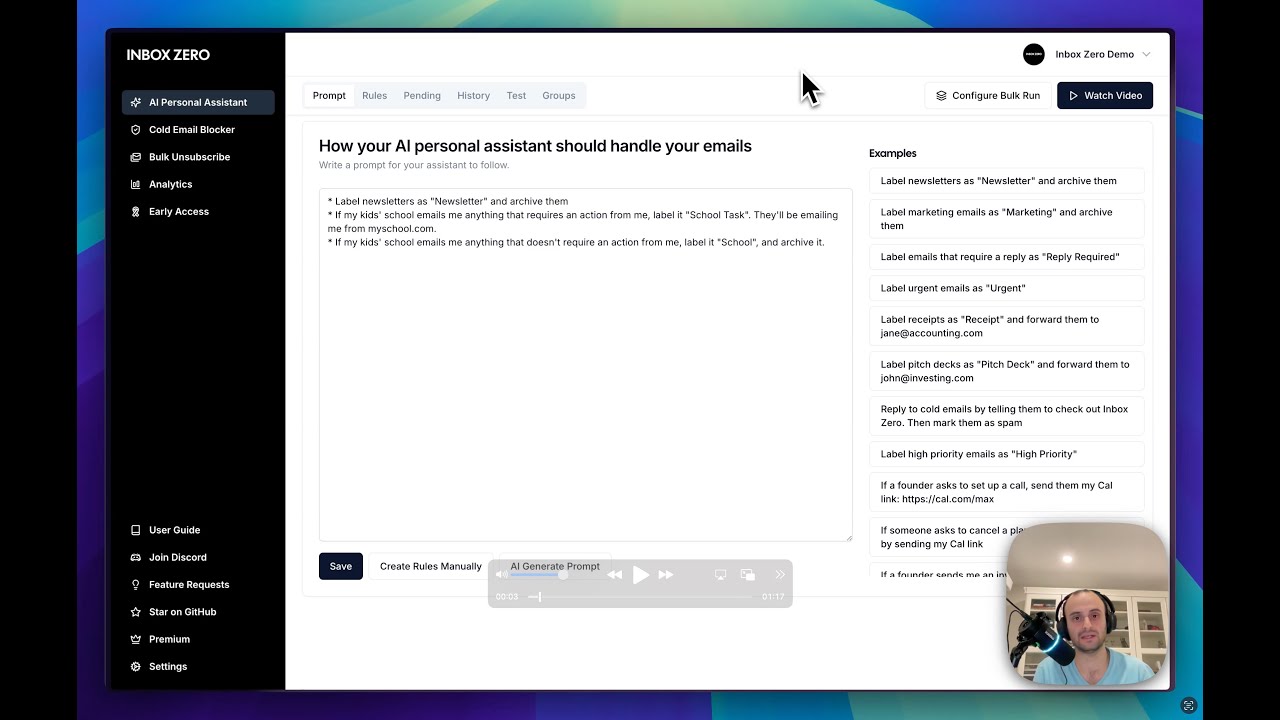
- AI Personal Assistant. It classifies, suggests, and pre-drafts responses in your voice. The AI doesn’t replace human judgment, but it removes the inertia of starting from a blank page.
- Cursor Rules for email. A plain-language rule system that tells the AI how to triage: what to prioritize, what to archive, when to follow up, and how to label.
- Reply Zero. A focused board that separates emails to reply to from emails awaiting responses, reducing the chance of forgotten threads.
- Smart Categories. Automatic categorization of senders and topics, speeding up bulk reviews or mass clean-ups.
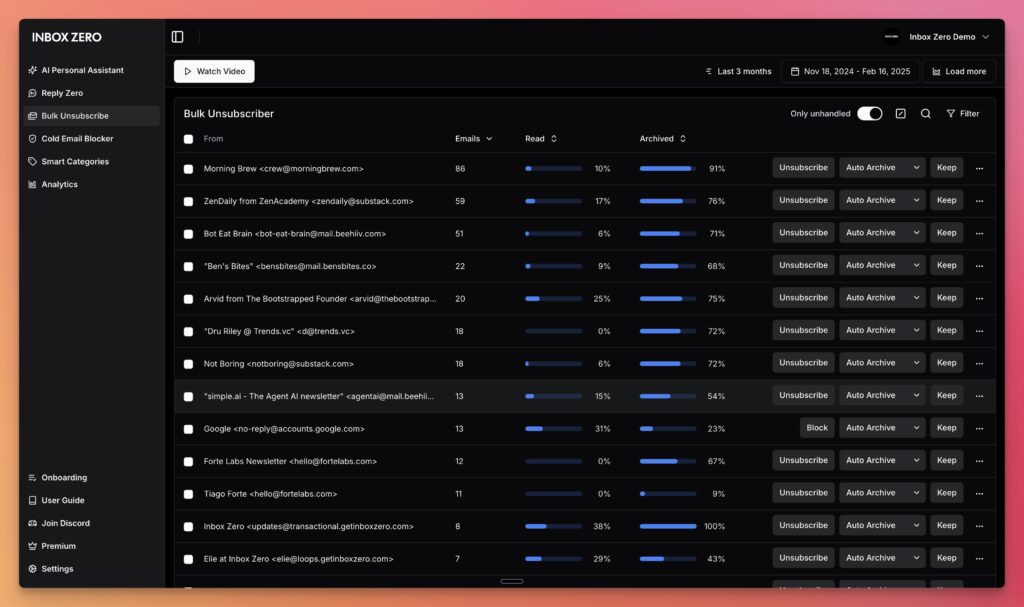
- Bulk Unsubscriber. A one-click unsubscribe and archive workflow that clears out long-ignored newsletters in batches.
- Cold Email Blocker. Automatic blocking of unsolicited mail to lower background noise.
- Email Analytics. Activity metrics and trend tracking to understand habits and improve personal workflow.
Taken together, these elements produce an inbox under control, where automation handles the repetitive tasks and the user retains the final say.
Self-hosted by design: privacy, keys, and compliance under your control
Inbox Zero is conceived self-hosted first. There’s a hosted edition for those who prefer zero ops, but the star of the show is running it yourself: Docker on a VPS, containers with clearly scoped environment variables, and encrypted OAuth tokens for Gmail or Outlook access. This architecture returns credential control and data surface to the team operating the tool—crucial for organizations with strict compliance, auditability, or data-sovereignty requirements.
Secrets and runtime configuration live in a .env file modeled after the repository example. Typical values include:
AUTH_SECRETfor internal auth,EMAIL_ENCRYPT_SECRETandEMAIL_ENCRYPT_SALTto encrypt OAuth tokens,NEXT_PUBLIC_BASE_URLwith the deployment URL,INTERNAL_API_KEYfor internal calls,- and connection strings for Redis and Postgres (or defaults spun up via
docker-compose).
Model providers are flexible: Anthropic, OpenAI, Bedrock Anthropic, Google Gemini, Groq (Llama 3.3 70B) or Ollama locally. With OLLAMA_BASE_URL and DEFAULT_LLM_PROVIDER=ollama, teams can favor a local model to balance latency, cost, and privacy—useful when email content never should leave the organization’s perimeter.
Gmail and Outlook done right: OAuth with explicit scopes
On the Gmail side, the setup runs through Google Cloud: create an OAuth client, configure the consent screen, add authorized origins (e.g., http://localhost:3000 for development), and define redirect URIs. Scopes typically include gmail.modify, gmail.settings.basic, userinfo.*, and contacts, enabling read, categorize, draft, and contact management without over-privileging.
For Microsoft Outlook, the project leverages Azure Active Directory: register a multi-tenant app, define redirect URIs (/api/auth/callback/microsoft and /api/outlook/linking/callback), and grant Microsoft Graph permissions such as Mail.ReadWrite, Mail.Send, MailboxSettings.ReadWrite, Contacts.ReadWrite, plus openid, profile, email, and offline_access. With credentials in hand, MICROSOFT_CLIENT_ID and MICROSOFT_CLIENT_SECRET go into .env.
The outcome is a secure connection to the two dominant email providers, based on OAuth with encryption, minimal necessary scopes, and a configuration pattern that is easy to audit and revert.
Real-time updates with Google Pub/Sub and scheduled watch renewals
One practical edge is real-time handling for Gmail via Google Pub/Sub. The steps are straightforward:
- create a topic and subscription,
- declare a push endpoint in your app (production domain or an ngrok tunnel in development),
- set
GOOGLE_PUBSUB_TOPIC_NAMEandGOOGLE_PUBSUB_VERIFICATION_TOKENin.env.
From there, changes—new mail, replies, archiving—flow into the app without constant polling. A route like /api/watch/all enables the watch process, and a small set of cron jobs keeps it fresh, pushes weekly summaries, and disables unused auto-drafts in the reply tracker. The Pub/Sub + cron combination provides operational reliability in production and a smooth developer experience locally.
Docker done thoughtfully: build-time vs runtime secrets
The Docker workflow shows attention to detail. When building the image, you must set --build-arg NEXT_PUBLIC_BASE_URL="https://your-domain.com" because Next.js embeds NEXT_PUBLIC_* variables at build time. Changing that URL later requires a rebuild. At runtime, the container receives sensitive variables (DATABASE_URL, AUTH_SECRET, GOOGLE_CLIENT_ID, and so on), strictly separating public compile-time values from private execution-time secrets. That separation reduces leakage risk and facilitates secret rotation.
For local development, docker-compose up -d spins up Postgres and Redis with minimal friction. After that, pnpm prisma migrate dev applies migrations, pnpm run dev (or turbo dev) starts the app, and a faster local production mode exists via pnpm run build followed by pnpm start.
A modern interface, a steady cadence, and an optional premium tier
The UI—Gmail client views, AI Assistant panels, and Bulk Unsubscriber—leans on Tailwind and shadcn/ui for a cohesive, accessible experience. The team maintains an active features log, public issues, and a Discord community to discuss the roadmap and coordinate contributions.
Some capabilities are marked premium. In self-hosted deployments, upgrading is as simple as making yourself an admin by adding your email to the ADMINS variable in .env, then visiting /admin. This unlocks advanced features and admin tooling while remaining on your own infrastructure.
Calendar on the horizon
Calendar integrations are a work-in-progress. For Google Calendar, the basic path is already documented: enable the API in Google Cloud and add the return URI (/api/google/calendar/callback). While not the flagship feature yet, its presence hints at a future where mail and schedule share context in the same console.
Why it matters: from “work about work” to a manageable flow
For professionals and teams who spend too much time managing email, Inbox Zero acts as an intelligent orchestration layer. The aim is not just faster replies—it is less mental overhead. AI drafts the first version; plain-English rules enforce a triage strategy; reply tracking closes loops; and cold-email blocking with bulk unsubscribes reduces background noise. Crucially, credentials are encrypted and deployments can remain on premises, aligning with security and compliance requirements without sacrificing modern automation.
Reasonable hurdles and adoption profile
As with any self-hosted project, a few basics are required:
- Node.js ≥ 18.0.0 and pnpm ≥ 8.6.12 for the tooling,
- Docker (preferably Docker Desktop on Apple M-series laptops),
- and comfort with Google Cloud and Azure to complete OAuth flows and permissions.
Those who want zero maintenance may prefer the hosted route; teams who value customization, security, and ownership will gravitate to self-hosting. The trade-off is explicit: more control requires a bit more setup. In exchange, you gain governance over data and the automations that manage it.
Bottom line
Inbox Zero offers a pragmatic, contemporary approach to taming email: AI where it helps, human-readable rules to keep control, metrics to improve, and an open stack you can understand, audit, and adapt. In an era of overflowing inboxes, it promises speed without surrendering privacy. For professionals and organizations unwilling to hand their mailbox to a black box, it’s an option that deserves a serious trial.
Frequently Asked Questions
Can it be fully self-hosted on a VPS or on-prem?
Yes. The project is self-host-friendly by design. With Docker and a well-scoped .env, you can run Redis and Postgres via docker-compose, apply migrations with pnpm prisma migrate dev, and launch in development with pnpm run dev or in a faster local production mode with pnpm run build and pnpm start.
Which AI models does it support, and how do I prioritize a local model like Ollama?
It supports Anthropic, OpenAI, Bedrock Anthropic, Google Gemini, Groq (Llama 3.3 70B), and Ollama. To favor Ollama locally, set OLLAMA_BASE_URL and DEFAULT_LLM_PROVIDER=ollama in .env. This minimizes latency and improves privacy by avoiding external inference services.
How do real-time Gmail updates work without constant polling?
Via Google Pub/Sub. Create a topic and push subscription pointing to your app’s webhook (a production domain or ngrok during development), then set GOOGLE_PUBSUB_TOPIC_NAME and GOOGLE_PUBSUB_VERIFICATION_TOKEN. The /api/watch/all route initiates the watch, and additional cron jobs keep the subscription alive, send weekly summaries, and clean up unused auto-drafts.
What security measures protect OAuth credentials and sensitive data?
OAuth tokens are encrypted using EMAIL_ENCRYPT_SECRET and EMAIL_ENCRYPT_SALT. Scopes for Google and Microsoft are scoped to what’s necessary (read/write mail, basic settings, contacts), and a self-hosted deployment ensures tokens and data remain on infrastructure you control, reinforcing compliance and operational control.