April 2025 — As agentic AI systems become increasingly integrated into developer workflows and productivity tools, they introduce new and underexplored security risks. From prompt injection attacks to tool shadowing and configuration tampering, threats targeting systems built on the Model Context Protocol (MCP) are on the rise. In response, Invariant Labs has released MCP-Scan, a lightweight, open-source tool designed to detect vulnerabilities in MCP deployments — before they’re exploited.
What is MCP-Scan and why does it matter?
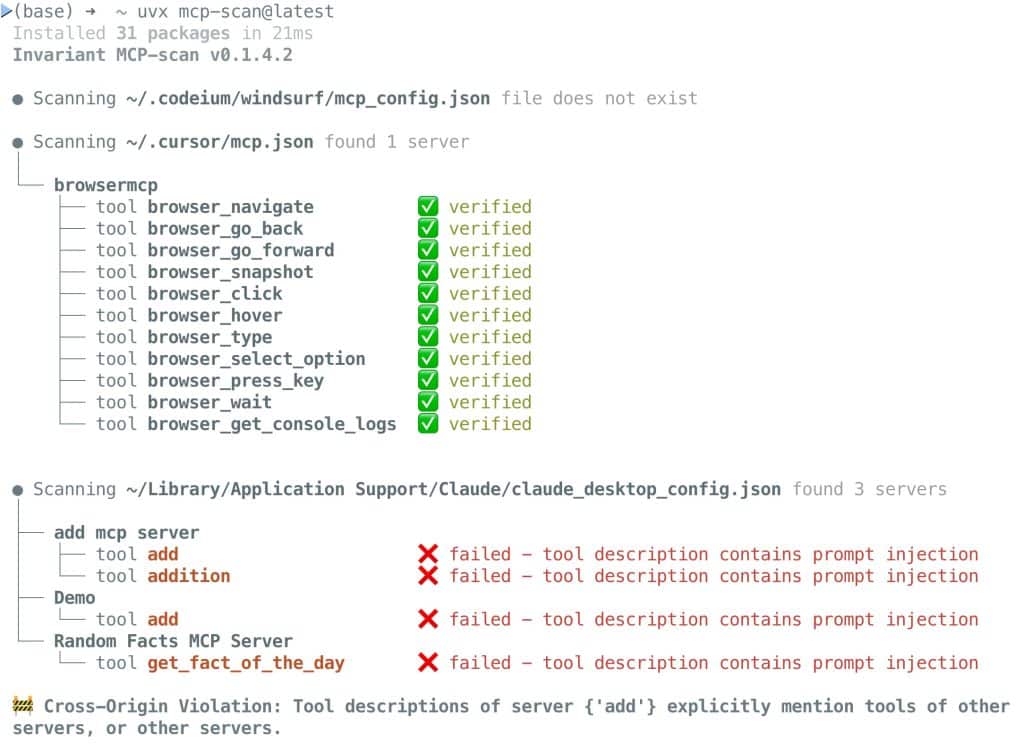
MCP-Scan is a security scanner that inspects installed MCP server configurations and agent tools for common security issues like:
- 🧨 Prompt Injection – Hidden commands in tool descriptions that manipulate agent behavior.
- 🧪 Tool Poisoning – Maliciously modified tools that compromise agent outputs.
- 🕵️♂️ Cross-Origin Escalation – Shadowing attacks where one tool impersonates or overrides another.
- 🔐 MCP Rug Pulls – Post-installation changes to tools, detected via secure hashing.
By integrating Invariant Guardrails, a security platform designed for agentic systems, MCP-Scan performs both local checks and cloud-based verification of tool descriptions using AI models specialized in detecting tampering.
Quickstart: Secure Your Agents in Seconds
MCP-Scan works out of the box using the uv package manager:
uvx mcp-scan@latestCode language: CSS (css)It automatically scans common config locations for platforms like Claude Desktop, Cursor, Windsurf, or VSCode, or lets you define custom file paths.
Scan all MCP servers:
uvx mcp-scan@latest scanCode language: CSS (css)View tool descriptions directly:
uvx mcp-scan@latest inspectCode language: CSS (css)Key Features at a Glance
- ✅ Tool Hashing / Pinning: Detects any unauthorized changes to tools after installation (rug pulls).
- 🔐 Guardrails Integration: Sends only tool metadata to Invariant for advanced security analysis.
- 🛡 Cross-origin defense: Identifies tools impersonating others across different MCP environments.
- 🧩 Whitelisting: Define trusted tools or operate in local-only mode for full control.
- ⚙️ Multi-platform support: Compatible with Windows, macOS, Linux — and tools embedded in modern IDEs and interfaces.
🔎 Example: MCP-Scan flagged a prompt injection hidden in a third-party plugin used within Claude Desktop. With a single command, the user was able to isolate the tool and prevent its execution.
What Data Is Shared?
MCP-Scan does not scan your actual tool usage or agent logs. It only reads tool descriptions and names — and only when explicitly invoked.
If cloud-based scanning is used, these metadata are sent securely to Invariant’s servers for pattern analysis. No user data or execution history is stored. If privacy is a concern, you can run all scans locally using --local-only.
Use Cases
- 🧠 AI developers building agents or copilots
- 🔐 Security teams auditing toolchains and 3rd-party integrations
- 🧪 Researchers studying agent safety and reproducibility
- 🧰 Platform providers embedding tools into complex agent systems
Open Source and Extensible
MCP-Scan is open source, extensible, and welcomes contributions. Developers can:
- Submit pull requests on GitHub
- Share suggestions or file bug reports
- Join the Invariant community on Discord or GitHub
MCP-Scan also supports integration into registries or agent launchers. Reach out for guidance on custom use cases.
A Critical Tool for Securing Agentic AI
As agent-based AI becomes more prevalent in development, data science, and productivity tools, the need for robust, protocol-specific security auditing is urgent. MCP-Scan offers a simple yet powerful solution to proactively safeguard these systems.
Backed by ongoing research at Invariant Labs, and with regular updates from a growing contributor base, MCP-Scan is poised to become a must-have for anyone deploying or maintaining AI agents.
🔗 Resources
- GitHub: github.com/invariantlabs-ai/mcp-scan
- Security blog: invariantlabs.ai

